- Joined
- 31.10.19
- Messages
- 1,150
- Reaction score
- 2,824
- Points
- 113

In Internationalized Domain Name (IDN) homograph attacks, characters from different languages that look almost identical, such as the Latin "a" and the Cyrillic "а" are used. At first glance, the result appears to be a normal domain or email address, but in reality, it involves substituting visually similar but technically different Unicode characters. When email service providers or authentication systems cannot properly distinguish these visually similar characters, it can lead to serious vulnerabilities, such as account takeover during registration, password resets or even bypassing 2FA protection, which poses a high risk if appropriate measures are not taken.
What the difference between Punycode attacks and IDN homograph attacks?
Punycode is a way to represent Unicode characters using only a set of ASCII characters (used in systems that don't directly support Unicode, such as the domain name system). IDN homograph attacks deceive the system (and sometimes the user) into thinking that two visually similar strings are the same, when in reality they are completely different.
Example:
"admin@example.com" vs "аdmin@example.com" - they look the same, don't they?
Required Tools
- Burp Suite - for intercepting and modifying HTTP requests
- Burp Collaborator - SMTP/email server
- Punycode Generator - for encoding Unicode characters
Step-by-step Exploitation Guide
Let's break it down step by step, from simple registration to full account takeover.
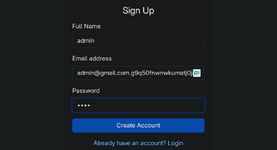
Step 1: Registration using a regular email address
Go to any site that supports email registration and register a new account. For the email, we will use Burp Collaborator, which acts as your fake SMTP server.After registration, log in using the same credentials to ensure the account works properly, then log out.
Step 2: Using Punycode in email and re-registering
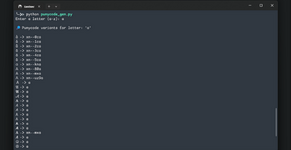
We will try to register again, but this time we will use Punycode characters in the email address. You can use the script - it will show all available Punycode characters along with their encodings. Just enter any character you want to convert and the script will generate the Punycode.
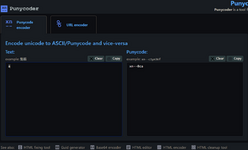
We just replaced the letter "a" in the email domain with "à" using Punycode generator. You can also check the result using any online Punycode decoder, such as Punycoder.
Step 3: Intercept and replace Punycode through Burp
Important note: Browsers like Chrome automatically encode special characters, making this trick impossible. Therefore, you need to use Burp Suite to intercept the request and manually replace the email address field with your Punycode version.
If the response says something like "Email already exists", it means that after normalization, the application considers the original address and the Punycode address to be the same. This is a clear sign of misconfiguration and potential vulnerability.
Step 4: Perform password reset through Punycode email address
Now go to password reset page. Enter the Punycode version of the email address and perform the reset through Burp Suite to avoid character encoding.
Step 5: Account takeover
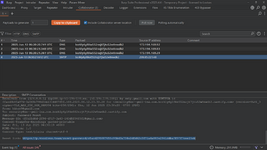
Send the request and in Burp Collaborator, you will see the SMTP call with the password reset link. Copy this link, open it in the browser and reset the password.
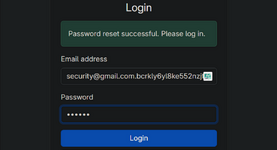
Now try logging in again, but this time using the original email address (not in Punycode format) and the new password you just set.
We just took over the account. Isn't this one of the cleanest and most dangerous account takeover methods you've ever seen? No user interaction, no phishing, no clicking on links. Just clever use of Punycode addresses. That's why it's considered a critical vulnerability and programs pay high bounties for its discovery.
Advanced method: Punycode in the username field
We have already seen how email normalization at the domain level can lead to account takeover. But what if the vulnerability lies in the username? This method is even more insidious because most developers don't check this part of the address properly, especially if it contains Unicode characters.
How it works:
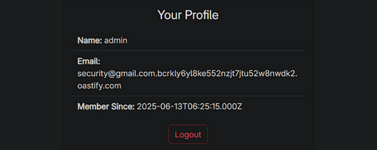
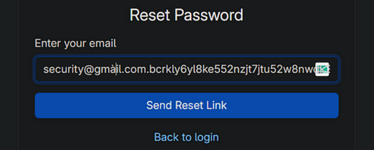
- This time, register using a username modified with Punycode, for example: ṡecurity@gmail.com.bcrkly6yl8ke552nzjt7jtu52w8nwdk2.oastify.com
- Use Burp Suite to intercept and modify the request, since browsers by default encode Unicode characters.
- If the server accepts this address and registers the account - that's the first victory.
- Then go to the "forgot password" form and this time enter the original version (withoutPunycode): security@gmail.com.bcrkly6yl8ke552nzjt7jtu52w8nwdk2.oastify.com
- If you received a password reset email in Burp Collaborator, it means the server considers both accounts to be the same.
Tip for bypassing 2FA: If the site uses 2FA and the application incorrectly processes email normalization (e.g, treats gmáil.com as gmail.com), an attacker can register as victim@gmáil.com, set up 2FA and then use their own 2FA code to log in to victim@gmail.com.
Mitigation
- Ensure strict email address validation. Allow only ASCII characters in email address input fields (e.g, using regular expressions or input sanitization libraries).
- Ensure email address normalization. Convert Unicode to ASCII (e.g, using IDN.toASCII() or similar) and apply normalization in all processes.
- Block IDN and Punycode if they are not needed. Reject addresses containing domains with Punycode prefixes (e.g, xn - example).
- Check the logic in registration, login and password reset processes. Ensure the same logic is used in all processes to avoid discrepancies and bypasses.
Conclusion
Attacks on IDN address using Punycode are one of the most powerful account takeover methods.
So using the right tools and approach you can discover serious vulnerabilities that many overlook.