- Joined
- 26.12.23
- Messages
- 247
- Reaction score
- 14,320
- Points
- 93

?️ d0ctrines OPSEC Codex: The Art of Digital Invisibility (Volume 3) - ?️ Hardwired for Stealth ?️ Pt 1
- Volume 1 - Vanishing Act 101 ?️
- Volume 2 - Ghosting the Inbox ?
- Volume 3 - Hardwired for Stealth ?️
- Volume 4 - Hidden Ledger ₿
- Volume 5 - TBD
If youve been following this OPSEC Codex series, you already know the basics of digital invisibility and email security. But guess what? Thats just the tip of the iceber. Welcome to Volume 3: where we dive into the end of hardware security.

Now before you start thinking this is some boring lecture about motherboards and CPUs let me stop you right there. When we talk about 'hardware' in this volume, were not just talking about the physical stuff you can hold in your hands. Were talking about the entire ecosystem - the devices, the software that runs on them, and how they all come together to either keep your ass safe or get you into trouble.
Why? Because in OPSEC, youre only as secure as your weakest link. You could have unbreakable encryption and the stealthiest online presence, but if youre running it all on a device thats leaking information like a sieve, you might as well be sending your activities directly to the feds.
In this volume well be looking at why your everyday devices are a ticking time bomb for carding and other sensitive ops. Well explore amnesic systems that leave no trace and well look at real life cautionary tales of people who thought they were untouchable - until they werent.

And dont think were just sticking to the digital stuff. In Part 2 of this installment were getting our hands dirty with the physical side of things. Well cover real, tangible steps you can take to protect your hardware. From choosing the right devices to keeping them secure in the real world, were leaving no stone unturned.
This isnt just theory, boys and girls. This is practical, real world shit that could mean the difference between success and a new set of stainless steel bracelets. So pay attention, because class is in session and ignorance in this game can cost you everything.
By the time were done you'll never look at your devices the same way again.
'Remember: these guides assume youve already sized up your own risks. If youre just dipping your toes with $5 gift cards, this level of security is overkill. But if youre swimming with the sharks, pay attention. We covered how to scale your security in Volume 1 - go back and read that shit if you havent. Know your threat level before you dive in.'
Why Persistence is a Liability
Youve heard the stories, right? Some hotshot hacker/carder thinking theyre untouchable, then BAM - the feds kick down their door and suddenly their whole digital life is spread out on an evidence table. One forgotten file, one overlooked cache and its game over. The difference between a slap on the wrist and decades in the slammer often comes down to whats on your hard drive.

OPSEC is like a clingy ex that just wont let go. Its the digital footprint you leave behind every time you use a device. And trust me, its a bitch to get rid of.
Lets talk about traditional hard drives for a sec. You know, those spinning platters that store data magnetically? When you 'delete' a file on these bad boys, youre not actually erasing shit. Youre just telling the system, 'Hey, its cool to write over this space when you need to.' But until that happens, your 'deleted' data is just chillin there waiting for some forensics nerd to come along and piece it back together.
Remember that scene in Mr. Robot where Elliot nukes his hard drives with a drill and his chips in a microwave? Funny as hell, but not far off from what youd need to do to truly wipe a magnetic drive. (Pro tip: Dont actually try this at home, unless you enjoy the smell of melted plastic and the possibility of starting a fire.)

Now, if youre not living in the stone age, youve probably got an SSD in your rig. These are a bit better when it comes to security. SSDs use a different technology that makes data recovery trickier, especially if youre using encryption.
Speaking of encryption, its your best friend - until it isnt.
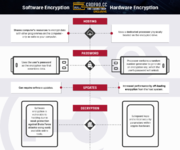
See, when youre using an encrypted drive, the decryption key is stored in your computers RAM. RAM, for those who slept through Computer Science 101, is like your computers short-term memory. Its fast, but it forgets everything when you pull the plug. At least, thats how its supposed to work.
Heres where it gets fucked up: During raids, feds have gotten smart. Theyll keep your machine powered on to prevent that RAM from clearing. Remember Ross Ulbricht, the Dread Pirate Roberts himself? Part of how they nailed him was by grabbing his laptop while it was still on, keeping those decryption keys nice and accessible in the RAM.
Persistence is a liability because its a treasure map to your dirty laundry. Every file you keep, every cache your system maintains is another way to hang yourself if things go sideways.
The Amnesic Advantage: Forgetting as a Superpower
Short version Amnesic Systems are like digital burner phones that forget faster than you after a night of heavy drinking.
Remember all that stuff we just went over about hard drives being treasure troves for forensics nerds? Amnesic systems say screw all that. Every boot-up is like using a brand new, never been used computer. No history, no saved passwords, no digital footprints to your shady activities.
Its a game-changer for anyone who values their privacy more than their Instagram likes. Journalists in war zones, whistleblowers exposing corruption, and yes, carders and hackers - we all benefit from the power of digital amnesia.
The real beauty of these amnesic systems is that they also route all your traffic through Tor right out of the box (or with minimal tweaking). There cant possibly be any leaks too, as these systems are tested daily. Using amnesic systems is hitting two birds with one stone: youre not just securing your ass from forensics, youre also telling the world to fuck off to anyone trying to snoop on your internet traffic. Its privacy on steroids that even the FED themselves cried multiple times about it.
Our three big guns in the amnesic world are Whonix, Tails and Qubes. Each has its own twist on privacy and security.

Whonix is the most user friendly of the bunch. It runs as a virtual machine, its like having a separate computer inside your main one. All traffic goes through Tor, making tracing your ass impossible. The catch? It relies on your host OS, so if your host is compromised youre screwed. Its good for anonymity if you know your way around VMs. Note that Whonix isnt amnesic by default, but you can toggle that feature on. Think of it as selective memory - good for longer term ops. Its also the most beginner friendly and easiest to use. Just run it alongside your main PC, switch to it when you need to do dirty work.
Tails is your USB ninja. It leaves zero trace on your hard drive, runs entirely from RAM. Boot from a stick, do your thing, shut down and its like you were never there. Feds come knocking just remove the stick and their plans are foiled. It comes pre-loaded with privacy tools, ready to go. Good for when you need to use a public computer without leaving a trace. The downside? Slow as molasses and long term storage is a pain in the ass.
Qubes is for the paranoid power users. Its not just amnesic - its a whole new approach to OS security. Imagine multiple personalities for your computer, each isolated. One part gets compromised? The rest stays clean. You can even run Whonix inside Qubes for extra anonymity. The trade-off? Its complex as hell, needs serious hardware and runs hot enough to fry an egg on your laptop. This is just for gigachad hardcore motherfuckers who run darknet markets or are on the run from INTERPOL/CIA. Dont use this shit if you dont know what youre doing!
Choosing between these is like picking your poison. Whonix for Tor lovers who dont mind VM setups and want memory options. Tails for true 'ghost mode' operations. Qubes for those who obsessives who want to compartmentalize every digital breath they take.In this game, forgetting isnt a bug - its a feature. These systems dont just cover your local tracks; they make you vanish from the government peeping toms entirely. But remember - no system is bulletproof. Each can still screw you over if youre careless. The most secure setup in the world is useless if you use it to log into your personal Facebook. So before you boot up that persistent system for some shady shit, ask yourself: Can you afford to leave a trace? More importantly, do you have the tech skills to use these systems right? In OPSEC, a misused tool is more dangerous than no tool at all.
Cautionary Tales: When Persistence Bites Back
Theorys all well and good, but nothing drives a point home like real-world fuck-ups. Lets take a stroll down the hall of shame and see what happens when you skimp on OPSEC and rely on persistent systems.
Remember Roman Seleznev, aka 'Track2'? This Russian carder thought he was the king of the cybercrime world, raking in millions from stolen credit cards. His downfall? A laptop packed with 1.7 million stolen credit card numbers. When the feds nabbed him in the Maldives, that persistent data might as well have been a signed confession. Now hes serving 27 years, all because he couldnt be bothered to use an amnesic system.
Then theres Alexsey Belan, one of the FBIs most wanted hackers. This guy was smart enough to hack Yahoo, but dumb enough to keep evidence on his devices. When law enforcement finally caught up with him, his persistent data trail led to a 15-count indictment. Dudes still on the run, but his digital fingerprints are all over the place.
Lets not forget Albert Gonzalez, the mastermind behind the TJX hack. This guy stole over 170 million credit and debit card numbers, but his persistent chat logs and stored data became his undoing. The feds recovered years of incriminating evidence from his devices. Twenty years in the slammer because he didnt understand the first thing about data persistence.
Even the notorious Carbanak gang, who stole over $1 billion from banks worldwide, got owned by data. When the authorities finally cracked their operation they found a goldmine of evidence on the seized computers - malware samples, victim data and internal comms. Their persistent systems became a roadmap for the prosecutors.
These arent just isolated incidents. The cybercrime landscape is full of the digital bodies of carders, hackers and fraudsters who thought they were too clever to get caught. They all learned the hard way that in the digital world whats done is rarely undone. Your persistent system isnt just storing your data - its building a case against you. Always reemeber: The feds are always snooping around waiting to get their opportunity.In the wise words of the rather unwise Takashi 6ix9ine:

There are only two things I fear. God and the FBI.
Conclusion: Forget to Remember
We've covered a lot here. In a nutshell? Leaving no trace is just as important as the job itself.
Persistent systems are digital fingerprints, unique to you and everywhere. Amnesic systems? Theyre your get out of jail free card, giving you a clean slate with each boot.
Whonix, Tails, Qubes - each has its pros and cons. But theyre tools, not magic wands. The most secure system wont save your ass if you use it like a moron.
Now hardware. Because all the software in the world wont help if your physical setup is compromised.
Always be paranoid, always be free. d0ctrine out.