- Joined
- 31.10.19
- Messages
- 1,145
- Reaction score
- 2,809
- Points
- 113

DARKINT expands OSINT capabilities by providing access to information that is absent from the surface web. The dark web operates on encrypted networks such as Tor and I2P, which provide user anonymity. These conditions make it a suitable environment for cybercriminal activity: stolen credentials are sold here, malware is distributed and attacks are discussed and planned. For organizations, dark web monitoring functions like an early warning system. Underground resources often host exploits, databases and attack tools long before they become known to the wider public. Additional value lies in understanding the tactics, techniques,and procedures (TTPs). Integrating DARKINT into an OSINT strategy makes analysis more complete. Investigators, cybersecurity professionals and law enforcement gain access to information from hidden segments of the network and use it to improve the effectiveness of investigations. Example: In 2021, advertisements offering a sample of LinkedIn user data appeared on the dark web. It later turned out that this was not a platform breach but a compilation of information from multiple leaks and open sources. Nevertheless, the sample size exceeded 700M records. Monitoring systems recorded the publications long before the full dataset emerged. This allowed analysts to warn companies about potential credential stuffing attacks and phishing campaigns, buying time to secure accounts.
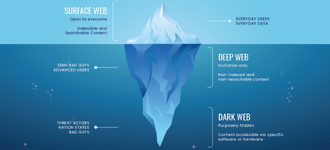
The dark web is immeasurable: most of the information is hidden, such as cybercrime, scam activities, hacking, illegal forums, etc.
Since search engines cannot index sites, anonymous web pages are not publicly available to display these sites in search results.
What can be extracted from the Dark Web
DARKINT provides access to various types of information, each useful for threat analysis in its own way:
- Tactics and attack methods (TTPs). Cybercriminals share exploitation experiences, discuss bypassing defensive measures and new anonymization techniques.
- News and talking points. Forums discuss a wide range of topics. This is an indicator of themes that might be used in phishing campaigns or social engineering.
- Service marketplace. On the dark web you can buy exploits, rent botnets, etc. Monitoring this offers enables forecasting which tools will soon be in circulation.
- Sale of data. Stolen databases, accounts and access to corporate systems are regularly put up for sale. For companies, this is a direct signal of compromises.
- Underground identities. Despite anonymity, users leave digital traces. Correlating this data allows building profiles of participants and tracking their activity.
How to conduct OSINT Research on the Dark Web
Effective dark web research within OSINT starts with understanding which sources matter for a particular investigation. These may be marketplaces selling illegal goods and services, forums for information exchange or hidden wikis that help find new resources. Once sources are identified, proceed to data collection and analysis. This can be manual browsing via the Tor browser with capturing information and screenshots, automated parsing using specialized tools or using ready-made monitoring platforms that track keywords and trends. Working on the dark web requires strict security measures. To minimize risks, use separate devices, disable scripts and plugins in the Tor browser and regularly update software, including VPNs and protective tools. Next comes deanonymization. Despite the high level of secrecy on the dark web, participant identities can be established by correlating digital traces. Analysts match email addresses, nicknames, cryptocurrency transactions and other data, allowing them to link specific accounts to real people and their activities. Then content analysis is conducted. Studying messages and discussions helps reveal not only facts but also intentions. Sentiment and language analysis makes it possible to understand participant's motivation, assess the sophistication of planned attacks and determine which tactics and techniques they intend to use. Finally, track cryptocurrency transactions. Financial flows often become the key to exposing criminal activity. Using blockchain analysis tools, investigators trace the movement of funds related to ransoms, data sales or attack financing. This helps reveal threat actor infrastructure, their connections and the scale of operations.
Tips for Integrating Dark Web Intelligence into OSINT
- The dark web operates on encrypted networks and monitoring it requires secure and specialized solutions such as Threat Intelligence platforms. They automate data collection, provide navigation across hidden resources and help maintain operational security.
- Dark web data are only part of the overall picture. Their value increases when correlated with information from open sources, social networks and internal detection systems. This approach builds a comprehensive view.
- Raw data alone are of limited use. They need to be integrated into existing processes: SIEM systems, threat analysis platforms or incident response procedures.
- Maintain continuous monitoring. This allows threats to be recorded as they emerge and enables near real-time response.
Conclusion
OSINT and DARKINT pursue the same goal but rely on different information sources. OSINT works with open data: websites, social networks, media, public databases and registries. Such collection doesn't require specialized access and captures what lies on the surface of the internet. DARKINT, by contrast, focuses on closed network segments. Primarily this is the dark web, where communication takes place in anonymous encrypted networks like Tor or I2P. Monitoring these resources uses specialized tools and platforms capable of safely collecting and analyzing hidden data. Combined, these methods form a complete intelligence picture: OSINT provides strategic understanding, while DARKINT delivers tactical signals. However, dark web data should not be treated as reliable by default. Forums are often filled with disinformation, fake listings and false leaks. Authenticity verification requires cross-referencing with other sources and applying analytical methods, otherwise there is a high risk of misidentification or wrong conclusions.





