- Joined
- 26.12.23
- Messages
- 223
- Reaction score
- 3,551
- Points
- 93

So far Ive covered the basics of AI antifraud systems - their patterns weaknesses and how to dance around their detection methods. But lets face it - sometimes youre just rolling the dice. Maybe you need the cardholder to have pristine history with the antifraud system. Maybe youre dealing with strict 3DS requirements or those pain-in-the-ass EU cards with SCA. Or perhaps the antifraud system is getting too familiar with your device fingerprint after a few days and few transactions.
In cases like these the resources needed to maintain a working method multiply faster than your profits. Youre burning through proxies constantly rotating antidetect browsers and praying to the fraud gods that your next attempt doesnt trigger a security flag.
What if I told you that theres a better way? This is going to be a two-part guide that will change how you approach carding forever. In Part 1 well get behind enemy lines - accessing these antifraud systems to understand exactly why your cards are getting declined and how to assess your transactions. In Part 2 well take it further and show you how to completely break their detection capabilities by poisoning their data.
Todays focus is on getting access and using these systems to your advantage. This isnt just about understanding how they work - its about using their own tools to check your cards before you burn them on hits.
Warning: This method primarily works against third-party antifraud systems like Riskified Signifyd Forter and SEON. If youre up against integrated processor antifraud like Stripe Radar or Adyen risk engine the effectiveness drops significantly since they have direct access to payment data and transaction patterns that third-party systems cant see.
Disclaimer: The information provided in this writeup and all my writeups and guides are intended for educational purposes only. It is a study of how fraud operates and is not intended to promote, endorse, or facilitate any illegal activities. I cannot be held liable for any actions taken based on this material or any material posted by my account. Please use this information responsibly and do not engage in any criminal activities.
AI Antifraud and Data
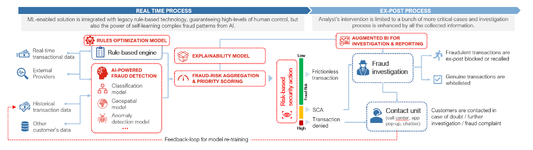
Lets get something straight - these AI antifraud systems arent just some fancy algorithms checking if your IP matches your billing address. Theyre massive data-hungry beasts that have been watching and learning from billions of transactions across thousands of merchants. Every time someone enters their card at any merchant using their service that transaction becomes another data point in their vast neural network.
Think about it: When you try to card something on a site using an antifraud system that AI isnt just looking at your current transaction. Its checking if that card has ever been used across ANY of their merchant partners. Every legitimate transaction builds trust every chargeback leaves a permanent scar in their database.
This is why sometimes your perfect setup still fails - that pristine high-balance card youre trying to use? Maybe its triggered a chargeback at some random dropshipping store three months ago. Or perhaps the real cardholder only makes small purchases under $100 and suddenly youre trying to buy a $2000 laptop. The AI sees these patterns and it remembers. Forever.
The data they collect is fucking insane - device fingerprints behavioral patterns transaction amounts time between purchases typical merchant categories... but at the core of their decision making is one simple question: "Does this transaction match the historical pattern weve seen with this card across our entire network?"
This is why running the same card repeatedly is suicide - even if you change everything else youre building up a profile in their database that screams "Im a fraudster". Each failed attempt is another red flag associated with that card number and your device fingerprint.
These fraud systems deliberately keep you in the dark never telling you the real reason your transaction failed. They wont say "Declined: This card had 17 failed attempts across our network in the past week" - they just hit you with that generic bullshit. Thats what makes them "black box" systems - you cant see inside their decision-making process.
But thats exactly why getting access to these systems is such a fucking game-changer. No more guessing why your Booking.com transaction got declined - youll have the same tools they use to make those decisions. Youll see exactly what triggered their alarms whether it was suspicious device patterns unusual spending behavior or that chargeback from three months ago thats still haunting the card. And in Part 2 well take this knowledge and use it to poison their data - injecting our own patterns and behaviors until these systems have no choice but to approve our transactions. Think of it as reprogramming their AI from the inside out.
Getting Behind Enemy Lines
Getting access to these fraud prevention systems is the biggest pain in the ass youll face - once you got this youre pretty much home free.
First you need to understand that these "enterprise-grade" systems are run by companies so desperate for growth that their sales teams would probably sign up a potato if it had a shop. Each provider has their own level of security and knowing which ones to target can save you weeks of wasted effort.
Dashboard URLs:
- Forter: portal.forter.com
- Signifyd: app.signifyd.com
- Riskified: app.riskified.com
- SEON: admin.seon.io
- Ravelin: dashboard.ravelin.com
Moving up the difficulty ladder youve got Signifyd and Riskified. These fuckers actually pretend to care about who theyre signing up. Theyll want to see a legitimate-looking business theyll verify your email and their sales team will actually try to talk to you. Nothing impossible but you better have your shit together and a solid business front.
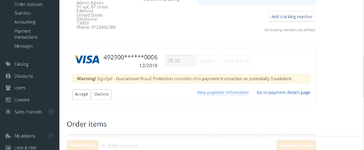
Then theres Forter - the final boss of antifraud access. These paranoid fucks want video calls business document verification and enough proof to make the FBI jealous. Unless youre planning to hit large-scale dont waste your time. The ROI just isnt there when you can buy logs for a fraction of the effort.
If youre still determined to get your own access (you stubborn fuck) heres what you need to do:
Grab a clean domain from Namecheap ($10-15 privacy ON) with a basic .com/.co TLD then set up a Shopify trial store in electronics or fashion - these niches blend in perfectly with high-value carding. Use AI to generate your business name product descriptions and docs swipe images from legit stores set up a professional firstname@domain email and create a boring-as-fuck LinkedIn profile. The more mundane and corporate your setup looks the better your chances of sliding through verification.
But heres the real shit that most guides wont tell you - unless youre planning something massive just buy the fucking logs. For a couple of bucks you can get dashboard access from any reputable seller. No paper trail no monthly fees no risk of fucking up during vetting and instant access to multiple providers. Just make sure youre buying from sellers who arent pushing burned accounts.

The whole point of this method is to be smarter than the average skid. Why build a whole fake business when you can backdoor your way in through existing access? Save that energy for what comes next - penetrating their dashboards assessing your transactions and actually poisoning these systems.
Assessing Your OWN Transactions
Now that weve covered getting access to these systems lets talk about what really matters - using them to check your cards before you burn them. But first you need to understand how these fuckers actually work under the hood.

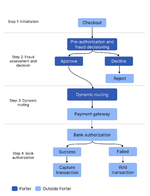
When a merchant uses an antifraud system they get three possible responses for each transaction:
- APPROVE - Transaction looks clean process the payment
- REVIEW - Suspicious but not clearly fraud needs manual review
- DECLINE - High-risk transaction that should be blocked
Along with these decisions merchants get a risk score from 0-100 and sometimes specific recommendations like "force 3DS" or "verify phone number."
The key thing to understand is that merchants control how strictly they follow these recommendations. Some will auto-decline anything over 50 risk score others might manually review orders up to 80. A few desperate merchants might even approve high-risk orders just to make sales.
This flexibility in merchant settings explains why the same card might work on one site but fail on another even when theyre using the same antifraud provider. A small electronics store might approve a $500 order that Best Buy would instantly decline.
But dont get cocky - these systems share data. A declined transaction at some random shop still gets logged in the antifraud network and can fuck up future attempts across all merchants using that provider. Thats exactly why were getting access to these systems first - so we can use their own AI to assess our transactions before we run them. Think of it as turning their own weapons against them - using their risk scoring to validate our setups before we burn cards on actual attempts.
Using SEON (And Other Antifraud Systems)
Every antifraud provider implements their shit differently. Signifyds API looks nothing like Forters and Riskified does their own weird thing. But the core concept is the same - you feed them transaction data they give you a risk assessment. Well use SEON as our example because theyre the most straightforward to work with and easiest to signup to. Make sure you have an account on SEON.io and a working API key. Run your terminal and make a CURL api call to their endpoint with the details of the transaction you want to assess.
The API Calls
Code:
$ curl https://api.seon.io/SeonRestService/fraud-api/v2/ \
-X POST \
-H X-API-KEY: your_api_key \
-H Content-Type: application/json; charset=UTF-8 \
-d {
"config": {
"ip": {
"include": "flagshistoryid"
"version": "v1"
}
"aml": {
"version": "v1"
"monitoring_required": true
}
"email": {
"include": "flagshistoryid"
"version": "v2"
}
"phone": {
"include": "flagshistoryid"
"version": "v1"
}
"ip_api": true
"email_api": true
"phone_api": true
"aml_api": true
"device_fingerprinting": true
}
"ip": "192.168.1.1"
"action_type": "purchase"
"transaction_id": "txn_123456"
"affiliate_id": "aff_78910"
"order_memo": "Test order"
"email": "example@domain.com"
"email_domain": "domain.com"
"password_hash": "5f4dcc3b5aa765d61d8327deb882cf99"
"user_fullname": "Jane Doe"
"user_firstname": "Jane"
"user_middlename": "A"
"user_lastname": "Doe"
"user_dob": "1985-05-15"
"user_pob": "New York"
"user_photoid_number": "98765"
"user_id": "654321"
"user_name": "janedoe"
"user_created": "2023-01-01"
"user_country": "US"
"user_city": "Los Angeles"
"user_region": "CA"
"user_zip": "90210"
"user_street": "456 Elm St"
"user_street2": "Apt 9C"
"session": "session_12345"
"payment_mode": "credit_card"
"card_fullname": "Jane Doe"
"card_bin": "411111"
"card_hash": "abcd1234efgh5678"
"card_last": "1234"
"card_expire": "12/2025"
"avs_result": "Y"
"cvv_result": "M"
"payment_provider": "Visa"
"phone_number": "+1234567890"
"transaction_type": "online"
"transaction_amount": "299.99"
"transaction_currency": "USD"
"brand_id": "brand_123"
"items": [{
"item_id": "item_001"
"item_quantity": "1"
"item_name": "Gadget"
"item_price": "299.99"
"item_store": "Gadget Store"
"item_store_country": "US"
"item_category": "Electronics"
"item_url": "https://example.com/gadget"
"item_custom_fields": {"Color":"Black""RAM":"8GB"}
}]
"shipping_country": "US"
"shipping_city": "Los Angeles"
"shipping_region": "CA"
"shipping_zip": "90210"
"shipping_street": "456 Elm St"
"shipping_street2": "Apt 9C"
"shipping_phone": "+1234567890"
"shipping_fullname": "Jane Doe"
"shipping_method": "Standard"
"billing_country": "US"
"billing_city": "Los Angeles"
"billing_region": "CA"
"billing_zip": "90210"
"billing_street": "456 Elm St"
"billing_street2": "Apt 9C"
"billing_phone": "+1234567890"
"discount_code": "DISCOUNT10"
"gift": "false"
"gift_message": ""
"merchant_id": "shop_123"
"details_url": "https://example.com/orderdetails"
"custom_fields": {}
}Their API will spit back:
Code:
{
"success": true
"error": {}
"data": {
"id": "67c2810c2de1"
"state": "DECLINE"
"fraud_score": 95.75
"blackbox_score": 93.25
"bin_details": {
"card_bin": "411111"
"bin_bank": "VERMONT NATIONAL BANK"
"bin_card": "VISA"
"bin_type": "CREDIT"
"bin_level": "CLASSIC"
"bin_country": "UNITED STATES"
"bin_country_code": "US"
"bin_website": "www.vermontnationalbank.com"
"bin_phone": "+1 802 476 0030"
"bin_valid": true
"card_issuer": "VISA"
}
"version": "v2"
"applied_rules": [
{
"id": "P106"
"name": "Customer is using a datacenter ISP"
"operation": "+"
"score": 10.0
}
{
"id": "P110"
"name": "IP address was found on 4 spam blacklists"
"operation": "+"
"score": 4.0
}
{
"id": "P112"
"name": "Customer is using public proxy"
"operation": "+"
"score": 10.0
}
{
"id": "E123"
"name": "Email is not similar to user full name"
"operation": "+"
"score": 1.0
}
]
"device_details": {
"os": "MacOS"
"type": "web"
"browser": "FIREFOX10"
"private": true
"platform": "MacIntel"
"user_agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:102.0) Gecko/20100101 Firefox/102.0"
"device_type": "desktop"
"screen_resolution": "1600x800"
}
"ip_details": {
"ip": "192.168.1.1"
"score": 24.0
"country": "US"
"state_prov": "California"
"city": "Los Angeles"
"type": "DCH"
"tor": false
"vpn": false
"web_proxy": false
"public_proxy": true
"spam_number": 4
}
"email_details": {
"email": "example@domain.com"
"score": 2.11
"deliverable": true
"domain_details": {
"domain": "domain.com"
"registered": true
"disposable": false
"free": false
"custom": true
}
}
"calculation_time": 2327
}
}Reading the Response
SEONs response tells you three crucial things:
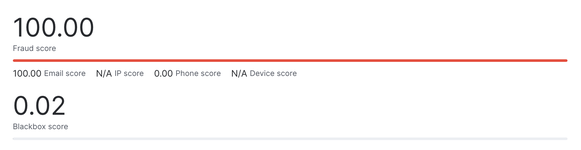
1. Fraud Score (0-100)
The score ranges from 0 to 100 where:
- 0-50: Low risk likely to be legit
- 51-80: Medium risk needs attention
- 81-100: High risk probably fraud
2. Applied Rules & Data Points
The response shows which default rules got triggered:
- email.disposable: Using temp mail
- email.quality: How legit the email looks
- ip.proxy: VPN/proxy detection
- ip.datacenter: Using datacenter IP
- card.bin_risk: BIN risk level
- velocity.ip: Too many hits from same IP
3. Suggestion
One of three possible actions:
- approve
- reject
- review
The response also includes detailed data points about why each rule was triggered letting you see exactly what raised red flags. This allows you to adjust your approach to get maximum success when hitting sites. On our next guide well cover how to poison these systems to make them approve your transactions better.
Remember: Each antifraud system has their own special sauce. Signifyd might put more weight on email age while Forter might care more about device fingerprints. The key is learning how to read their responses and adjust your approach based on what theyre flagging.
Other Providers
Different antifraud providers have their own unique API setups each with its quirks and requirements. Heres a sample of how to send transactions to some of the major players:
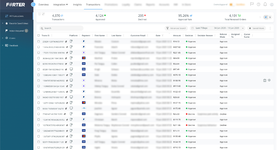
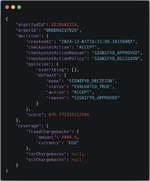
Here's an example of me assessing the information of my card for Signifyd before committing to using it on a Signifyd site. See how they approved it for $4,000? That means I can easily hit below 4,000 for any site powered by Signifyd with the same details and get away with it.
If you already have access to any of these systems either by self-reg or logs and need help with implementation hit me up on Telegram.
Whats Next?
While our previous guide showed you how to dodge these AI systems from the outside this time we went deeper - straight into their guts. You now understand how merchants talk to their antifraud providers how risk decisions get made and most importantly how to access their dashboards to check your own cards before burning them.

But knowing how to read these systems is just the beginning. In Part 2 were going to break them completely. Youll learn how to poison their training data build trusted profiles and make their AI work for you instead of against you.
With these guides these systems arent black boxes anymore - youve seen how they work from the inside. Time to make them dance to your tune.
Stay tuned for Part 2. d0ctrine out.
Last edited: