- Joined
- 31.10.19
- Messages
- 857
- Reaction score
- 1,861
- Points
- 93
Today we'll practically try out some tools and attempt to learn more about a person based on nickname.
Since the only input we have is a nickname, I suggest we run it through two good tools for this purpose.
Maigret
Since the only input we have is a nickname, I suggest we run it through two good tools for this purpose.
Maigret
Maigret is an innovative tool specifically designed for analyzing data from various social platforms. It provides extensive capabilities for gathering information, analyzing user activity, finding connections and other functions. This tool has flexible settings for data collection and analysis, allowing you to choose social networks and save results to files. Maigret supports over 3000 sites for searching by nickname. An excellent tool for nickname searching, it installs very easily and is just as easy to use.
Bash:
pip3 install maigret
maigret username
Bash:
git clone https://github.com/soxoj/maigret && cd maigret
pip3 install -r requirements.txt
./maigret.py username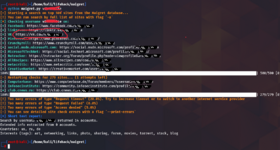
Already not bad, we found an account on a social network and some popular services like Pinterest.
Mr.Holmes
Mr.Holmes is a project aimed at gathering information from open sources about social networks, phone numbers, domains and IP addresses using Google Dorks. The next tool is named after the well-known detective and I can say that it's worth attention. It can be installed on both Linux and Termux on Windows. We will, of course, consider the Linux option.
Bash:
git clone https://github.com/Lucksi/Mr.Holmes
cd Mr.Holmes
sudo apt-get update
sudo chmod +x install.sh
sudo bash install.sh
python Mr.Holmes.py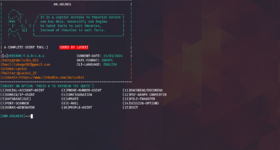
Choose option 1 and then it will ask if we want to use a proxy; I don't use a proxy and will decline. Next, I will choose the first search method. After the search, the tool will also ask if we want to go through the dorks, send a report of the search to someone and if we want to encrypt our report.
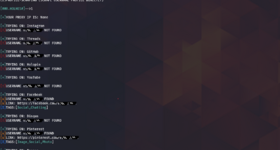
The tool has a very nice feature of maintaining a local database. Let's take advantage of our database and select option 5.

As we can see, the database server has started on port 5001. When we go to this address, a login form for the database management panel will pop up, with the default being Admin Qwerty123.
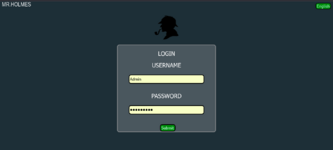
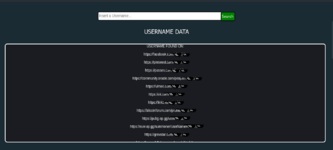
We select the search by Username and enter the nickname we used for the search.
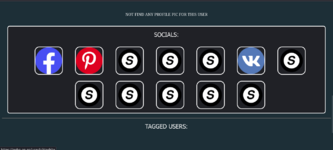
As a result of the investigation, we can also obtain the user's avatars and compare them with other services. We can also use the PEOPLE-OSINT option under number 10.
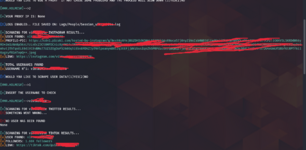
Here we also have detailed logs of the search.
Holehe
Holehe is a powerful tool for discovering registered accounts by email. Holehe checks for the presence of email binding to accounts on various platforms, including Twitter, Instagram, Imgur and over 120 other sites. This tool is installed and used in a very simple way.
Bash:
pip install holehe
holehe email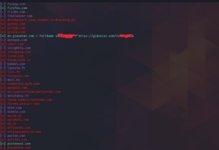
As we can see, the services match those we found earlier when searching by nickname, so we are on the right track.