- Joined
- 26.12.23
- Messages
- 247
- Reaction score
- 13,405
- Points
- 93

? The Problem with RDPs ?
Lets cut through the bullshit about RDPs because holy fuck the amount of confusion I see in forums and Telegram groups is giving me an aneurysm. Every day some newbie slides into my DMs asking if RDPs are the magic bullet for carding or if they should ditch their antidetect setup for muh RDPs.
Heres the raw truth: RDPs arent some mystical hacking tool thatll instantly transform you into a carding god. Theyre just another weapon in your arsenal - one thats frequently misunderstood misused and oversold by every sketchy Telegram vendor trying to make a quick buck off your ignorance.
So grab your favorite energy drink and settle in. Were about to deep dive into the world of Remote Desktop Protocol - the good the bad and the 'holy shit why didnt anyone tell me this before?'
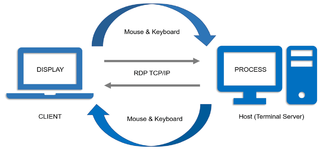
What The Fuck is an RDP?
At its core RDP (Remote Desktop Protocol) is your digital bridge to someone elses computer. You get full access to a machine somewhere in the world - mouse keyboard screen the whole fucking package. On paper this sounds like a carders wet dream right? Instead of spending hours fine-tuning an antidetect setup you get handed a 'clean' machine ready to run your operations.
But not so fucking fast.
Heres where shit gets real: Most of whats being sold as 'RDPs' in online arent the pristine machines you think they are. Let me paint you a picture of whats actually happening behind the scenes:
Datacenter RDPs
Picture a massive datacenter. Row after row of server racks humming away with hundreds of virtualized instances. That 'Windows 10 RDP' you just bought? Its probably just another VNC session running on an oversold server sandwiched between 50 other 'clean RDPs' on the same hardware.
This setup has more red flags than a Soviet parade:
- Datacenter IP address (instant red flag) ?
- Virtualization fingerprints are a dead giveaway that youre not on real hardware
- Your 'unique' machine is sharing resources with god knows how many other carders
- The hardware signatures are a flashing beacon to any half-decent antifraud system
So whats the fucking difference between this and running your own VM? There isnt one. Youre just paying premium prices for the same shit sandwich except now youre trusting some random vendor with full access to everything you do.
Botnet RDPs
Now were getting to the good shit - botnet RDPs. These are provided by botnet operators whove infected real computers belonging to random people who probably still use 'password123' as their login. Instead of some half-assed VM in a datacenter you get a ghost session running on Karen from Wisconsins Dell laptop through hVNC.
Why is this better? Because youre piggybacking on a legitimate machine:
- Real residential IP address ✓
- Authentic hardware fingerprints ✓
- Genuine browser canvas signatures ✓
- Actual human-like behavior patterns ✓
Sure these RDPs cost more than your typical datacenter garbage. But in fraud like everything else you get what you pay for.
But like everything else in fraud its not always rainbows and butterflies. Botnet RDPs depending on where you source them from will most likely suck ass. To understand why lets first look into how the botnet marketplace works...
The Botnet Marketplace
So what makes these infected machines not viable for carding? It all starts with distribution. Some career malware operator drops their payload through Google ads infecting thousands of computers. But instead of keeping these machines for themselves they see dollar signs and start wholesaling access - and thats where everything goes to shit.
Think of these infected RDPs like stolen cards getting resold through multiple shops. Each time they change hands they get dirtier:
- Original malware operator sells bulk access to multiple RDP shops
- Those shops slice and dice selling to different customers
- Multiple customers buy them for fraud purposes
- Rinse and repeat until that machine is digital roadkill
By the time you buy your 'premium' RDP that poor bastards computer is a digital warzone:
- Three different keyloggers fighting over who gets to steal passwords first
- Competing RATs playing tug-of-war with the mouse
- Crypto miners turning the CPU into a space heater
- More backdoors than a strip club
And we havent even gotten to the reliability issues. Remember Karen from Wisconsin? She might decide to shut down her laptop while youre trying to cashout some bank logs because her favorite soap opera is on. Or maybe her kid needs to play Fortnite. Or her antivirus finally grows a pair and nukes all the malware. RIP.
Proxies + Antidetect or RDP?
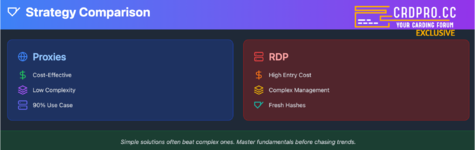
So after all this doom and gloom the million-dollar question remains: Should you stick with proxies + antidetect or jump into the RDP cesspool?
Heres the raw truth: If you absolutely need fresh non-unique Canvas/WebGL hashes because youre hitting the same antifraud systems repeatedly (like hammering Stripe hour after hour day after day) then yeah a proper botnet-sourced RDP might be your play. Assuming you:
- Have a reliable RDP provider
- Know how to verify youre not getting datacenter garbage
- Understand the risks of working with compromised machines
- Have the bankroll to handle constant replacements
But for 90% of carding operations? A solid understanding of proxies and antidetect browsers will do just fine. Ive written extensively about both - master those fundamentals instead of burning cash on unreliable and dirty RDPs.
Remember: Just because somethings more expensive or complicated doesnt make it better. Sometimes the simple solution is the right one. Focus on learning the basics before you start chasing every shiny new 'solution' that pops up in your Telegram feed.
The Bottom Line
Look I know youre eager to level up your fraud game. But heres the reality check you need: Fancy tools dont make the carder. Just because some Telegram guru is hyping up RDPs as the real shit doesnt mean you need to burn your bankroll chasing that dragon.
Master the fundamentals first. Learn how proxies work. Understand antidetect principles. Build a solid foundation before you start throwing money at every shiny new 'solution' that slides into your DMs.
Because at the end of the day its not about having the most expensive setup - its about knowing how to use what youve got. And sometimes the simple solution is the smartest play.
Now get back to studying you degenerate. d0ctrine out.