- Joined
- 31.10.19
- Messages
- 1,384
- Reaction score
- 4,662
- Points
- 113
Let's start with simple truths and try to propose the idea that in some cases using a proxy can be more reliable than a VPN. Therefore, first let's talk about the difference between a proxy and a VPN. It can be clarified that these are not really proxies only but proxy-based tools. I suggest starting with terminology.
What is a VPN?
Initially, VPN technology wasn't created specifically to bypass blocking but was (and still is) a tool that allows you to create a "tunnel" between several devices in order to unite them into a common network. You can draw an analogy with your home local network where all devices are connected to the same network and can exchange data with each other or connect to servers on the internet through a "router". In the case of a VPN, a similar network is built but doesn't work over Wi-Fi or wires in your apartment (but over the internet or other networks). And any of the devices connected to it can act as a "router". Most often the configuration is used when there are only two devices: yours and the server that works as a "router". As a rule, it's also a server which you connect to when setting up a VPN connection (but it doesn't have to be the same server).Among other things, it helps people exchange data while in different places - for example, in different cities, countries and even continents. Additionally (if you use your own VPN) this increases security, because Most VPN implementations use fairly strong encryption. There are many protocols for building a VPN and each of them has both it's advantages and disadvantages. In general, the most basic difference between a VPN and other communication technologies is that a kind of virtual network is built between devices (even if there are only two of them).
So, what about Proxy?
A proxy server is an intermediary server that accepts your requests, executes them on it's own behalf and transmits the results to you. You (more precisely, your programs/OS) "address" it and say: “I want to make such and such a request to such a server". He makes this request for you (in fact, there are some nuances but for simplicity I will omit them) and gives you the result. There are several types of Proxy servers, each of which has it's own characteristics and areas of application. There are quite a large number of proxy protocols but let’s take the most common ones and those that have maximum support from programs and the OS.
SOCKS (or rather SOCKS4 and SOCKS5 with it's modifications), HTTP and HTTPS.
VLESS, VMess, ShadowSocks (or new generation proxy) - we'll talk about it below.
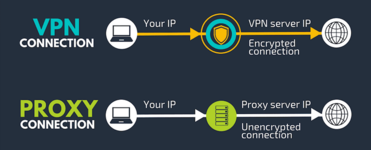
HTTP proxies operate using the same protocol as most websites, so it's spread was greatly helped by the fact that it was fairly easy to add support for (especially in browsers). And also the fact that it's use allowed content to be cached, which in some situations allowed users to get content faster. But this was at a time when traffic wasn't encrypted. Since then, the world has changed following the need to encrypt traffic. This is how HTTPS appeared - both as a protocol as a whole and as a proxy based on it. Essentially, this is the same HTTP but inside an encrypted tunnel (using TLS technology, formerly SSL), which is quickly established when connecting to the server. In addition to encryption, HTTPS also uses confirmation of the authenticity of the server, which provides it's "authentication certificate" certified by Trusted Certification Authorities (whose authentication and certification certificates are supplied with the OS and browsers, which have their own copy). Thus, if you make a request to an HTTP site (just through your ISP, without a proxy), then whoever is connected to your network + your ISP + their ISP's ISP (and so on all the way to the target server) sees everything: what you send in this request and everything you receive in response (including passwords). In the case of HTTPS, all data is transmitted already encrypted and isn't visible to those connected to the network. The same is true in the case of a proxy: if you use an HTTP proxy (not HTTPS) then the provider’s equipment sees all the transmitted content. And even if you access an HTTPS site through it, the listening equipment can see at least the site’s domain (and it can apply blocking). In the case of an HTTPS proxy, all that's visible to "eavesdroppers" is only the address of the proxy server. SOCKS4/5 proxies work a little differently, but in general the principles are the same.Let’s now try to figure out how VPN and proxy (as technologies) differ from each other.
Firstly, at a deep level (which isn't always visible) the most important difference is that:
VPN is a virtual network built on top of the Internet (or other network). Roughly speaking, let us remind you that it's similar to your home network with Wi-Fi and a router. It can have two devices (you and the server) or more - but the idea is that a virtual (but almost full-fledged) computer network is built between them. And through this network you can pass all your traffic - in this case, the server works as an analogue of a "router" in your home network. Installed programs, as a rule, have no idea how they access the network and don't see the difference between whether they access the network through a router, mobile Internet or VPN.
Proxy is just a program that accepts special requests (and responds to them) to either fulfill a specified web request or configure a connection to a specified service (being at the same time an intermediary). And this implies the presence of support for working through it in each specific program where it's intended to be used, which also allows for more fine-tuning of it's use. Allowing not only different programs to simultaneously work through different proxy servers, but also (in the case of browsers) even different specific sites within the same browser to be accessed through different specific proxy servers. This allows you not only to increase privacy, but (in the case of mobile devices) not to keep the application connecting to the VPN constantly running (and not to waste battery power on this, as well as unnecessary traffic to maintain the connection).
Secondly, modern VPN protocols mostly use encryption when building a connection.
While the main proxy protocols (old generation) for the most part don't encrypt traffic.
The exception - the type of HTTPS proxies described above, which use HTTP over TLS.
If used carelessly, this can endanger privacy and the user as a whole. Also, without encryption there's a high chance that you will not be able to bypass the blocking - since both the provider see where the connection is taking place. However, in the case of a "new generation" proxy, in the application in which the proxy is used, encryption is not necessary and it's absence is rather beneficial - because allows you to avoid unnecessary repeated encryption, which has a positive effect on the speed of data exchange. Since VPN programs encrypt data (sometimes in several "layers"), depending on various factors, the connection speed may be lower than through a proxy. However, modern devices allow VPN applications to encrypt data at speeds close to "average" internet connection speeds and you will most likely notice the difference only if you are used to very "wide" internet channels. The remaining differences, by and large, are consequences of those already listed and boil down to purely technical issues.

However, that's not all! We talked about "regular" proxies and "regular" VPNs. But the story would not be complete without mentioning "new generation proxies" (or let’s call them semi-proxies). Their essence lies in the fact that at a basic level they are proxy servers, but at the same time they also carry part of the VPN idea. In particular, the construction of an encrypted tunnel between the user device and a remote server.
I suggest that many have heard about the Shadowsocks protocol, which is this "new generation proxy". It was created on the basis of a SOCKS5 server with the addition of encryption - in the form of building an encrypted tunnel (as in the case of VPN) but without organizing a network, transmitting only proxied traffic in it. This allowed users from many countries to bypass blocking with virtually no loss in speed and also remain invisible (as was the case at the time of it's appearance) for DPI equipment. But this could not continue for long and DPI analyzers eventually learned to detect it. Therefore, enthusiasts have created a sufficient number of similar tools and "transports" for masking traffic. Shadowsocks is also evolving, offering new methods of camouflage.Among similar tools created after Shadowsocks, the most famous ones include V2Ray. However, V2ray had a fork V2Fly, on the basis of which the no less famous XRay was subsequently created, which is a "mutant" and collects various difficult-to-kill protocols used to build and masking the encrypted tunnel in which the proxied traffic is transmitted. The two famous protocols are also worth mentioning: VMess and VLESS. VMess was originally designed to bypass Internet censorship and securely and anonymously transfer data and has built-in encryption and support for various types of transports. VLESS is it's lightweight and newer version without built-in encryption, where the main advantage is performance and minimizing latency. Due to the fact that Proxy-based tools are actively developing precisely in the direction of masking traffic, they are a more reliable tool than VPN. In the meantime, you can configure XRay, using software such as Amnezia VPN (for a self-hosted solution) or ready-made solutions.
Last edited: