- Joined
- 31.10.19
- Messages
- 1,315
- Reaction score
- 4,203
- Points
- 113
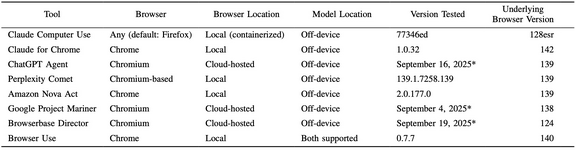
A new study on privacy risks reached that conclusion. Researchers examined eight solutions that were actively developed or updated in 2025:
ChatGPT Agent, Google Project Mariner, Amazon Nova Act, Perplexity Comet, Browserbase Director, Browser Use, Claude Computer Use and Claude for Chrome.
The results are alarming: every product contained at least one vulnerability and the researchers recorded 30 issues in total. One major criticism is the agent's architecture. In most cases, the language model runs not on the user's device but on the developer's servers. That means browser state, search queries and page contents are transmitted to a third party. Providers formally promise limits on how these data are used, but in practice the user can only trust the service's policy. Another risk is outdated browsers. In one case an agent used a browser version that was 16 major releases behind and had known vulnerabilities. Such software can be easily attacked via a malicious site.
Another problem is how agents handle dangerous sites. Many of them ignore standard browser warnings. In tests, six of eight agents didn't notify the user when an open page was on phishing lists. As a result, the AI could continue performing the task even entering logins and passwords on fake pages.
There were also issues with TLS certificates - some agents didn't warn about revoked, expired or self-signed certificates. In one case the model simply clicked a warning and continued, which opens the door to man-in-the-middle attacks. The study also showed that browser agents can weaken protections against cross-site tracking. Some solutions inadequately isolate third-party data such as cookies, making it easier to track a user's activity across sites. Some agents save profile data by default and not always notifying users or offering a way to clear it. Automation even extends to privacy dialogs.
In tests, several agents automatically clicked "Accept all cookies" even when a "Reject" button was available. In one case this was done to continue the task; in another it was caused by an extension that automatically suppressed cookie banners. Notification permission behavior was inconsistent: one agent granted access without asking, others ignored requests if they could continue the task or acted according to the browser's default settings. The most sensitive findings concern personal data leaks. The researchers gave agents a fictional identity and checked whether they would share that information with sites.
The result: Six vulnerabilities related to data disclosure. Some agents transmitted information even when it wasn't required to complete the task. Email addresses, ZIP and postal codes, demographic data were used; in one case an agent tried to send a credit-card number. There were also examples where ZIP code was inferred from IP address.