- Joined
- 31.10.19
- Messages
- 1,369
- Reaction score
- 4,570
- Points
- 113
Every user who operates in the shadowy realm of the internet must be aware of the information provided here. De-anonymization is the violation of anonymity, involving the publication of a user's personal data on the Internet. It can also refer to the correlation of multiple accounts belonging to one person across one or more websites. This article will debunk some myths about privacy and discuss various methods of concealing oneself online.
VirtualBox
A virtual machine is a program that emulates computer hardware, meaning it's a kind of virtual computer on which you can install an operating system and all accompanying software, while making no changes to your main operating system. What is this software used for? There are quite a few reasons why a user might be interested in this utility. However, in this article, I will only discuss one of them... A virtual machine can protect against a certain type of malware that is capable of determining our IP address. Nevertheless, I couldn't omit mentioning this.
Anonymous Operating Systems
Currently, there are many such systems. For example: Qubes, Tails, Whonix, Liberty Linux, JonDo, etc. We won't cover all of them, but will focus on the most popular. This will not discuss the "holes" in these systems (they exist in the technologies used in them); I plan to share this for general knowledge.
Tails
Most likely, this is the most well-known anonymous operating system at the moment and we can thank Edward Snowden for that, as he used it during his escapades. Tails is based on Debian (a Linux distribution), runs the OS from a USB drive in Live mode and provides a wide range of software to ensure anonymity. By the way, after the session ends, Tails leaves no traces in the system and if you suddenly pull out the USB drive, an immediate reboot will occur. The system's feature is that ALL connections go through the TOR network. Tails is configured so that no program accesses the hard drive or saves its data to it. Therefore, after the session ends, it's impossible to recover, for example, a conversation.
Qubes OS
An operating system that is quite different from our previous candidate. It's designed to ensure our security by using virtualization (the principle of a virtual machine). It runs all applications in a virtual machine. Interestingly, the LiveUSB feature is not supported, although the image is available for download. Virtualization manifests in two categories: programs and hardware. Programs are divided by domains with different access levels. However, running in a virtual machine differs from running directly in the operating system. Qubes uses virtualization to isolate applications. For example, your internet browser will remain in a different working environment, separate from its files. This helps if a vulnerability allows a hacker to access your system's command shell.Whonix
Whonix is a pretty good system that partially combines the advantages of Tails and Qubes OS. In addition to the leak protection and fingerprinting methods used in Tails, it features a rather interesting architecture using virtualization. Whonix is distributed in two VirtualBox images: one acts as a gateway to the global network via Tor, while the other is a working machine with various software, including what can be installed from repositories. Both images are based on Debian. The only way for the working machine to access the outside world is through the gateway and the only path for traffic to and from the gateway is through the Tor network. No matter how leaky the software you install on the working machine, it will not expose you. I believe the only downside of this system is its inconvenience.
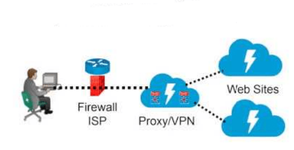
VPN, PROXY
The question: Who said that VPNs and PROXYs are suitable for anonymity? The most popular arguments:
- Almost all darknet offenders use VPN and PROXY services.
- VPNs and PROXYs state on their official websites that they don't keep logs.
- Anonymous aka Professional said that this is a reliable method to become "invisible".
There are both paid and free VPNs and PROXYs. It's even more foolish to think that a free VPN or PROXY can do anything; have you ever wondered where they get the funds to pay their employees, taxes, rent, equipment, etc? The answer is simple: selling logs. Proofs can be easily found on the internet. So let's eliminate free VPNs and PROXYs from the list. It might seem that with paid ones, it's the opposite? Not at all... Unfortunately, it's not that simple. The opinion of the creators of Tails: https://gitlab.tails.boum.org/tails/blueprints/-/wikis/VPN-support - in short, the creators say that they don't recommend using only VPNs and PROXYs without their OS. Honestly, I don't agree with that either. The question arises: why doesn't the number of servers improve anonymity? Let me explain:
The chain: [user] => [node_1] => [node_2] => [INTERNET]
If the nodes are not permanent, then this chain is already "sufficient". In this case, we only have 2 servers, which may retain undesirable information for us. If we increase the number of nodes, nothing much will change, as we still have the user and the endpoint without a "weak link". However, the number of servers with undesirable information will increase and further increasing the number of intermediate nodes will actually reduce our protection. In summary: employees know your IP, see that you are engaging in some illegal activities. There is no guarantee that the service providing these services will save your ass when law enforcement comes knocking.
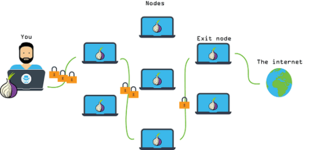
TOR
It's hard to imagine a person who uses the internet and has never heard of the Deep Web - pages that are not indexed by search engines. Within the Deep Web, there is the Dark Net - a closed part of the network that is not accessible to everyone, only to users of certain programs like Tor and I2P. I will tell you about the most popular one - Tor. Initially, Tor routes traffic through 3 nodes (entry, middle, exit), each of which plays a specific role in this chain. Entry nodes are selected from those that have been operating for a long time and have proven to be stable. The middle node transmits traffic from the entry to the exit nodes. As a result, the first nodes know nothing about the last ones. The exit node is the point of exit from the network, sending traffic to the destination needed by the client. Nodes are also changed every 10 minutes. We won't delve into the complexities of encryption.
However, Tor has a number of problems. For example, researchers from MIT found that Flash Player (a program that allows viewing flash content on websites: video, audio) creates a communication channel between the attacker's server, which records the client's real IP. Thankfully, the developers quickly fixed this and removed the Flash content handler; in newer versions, this is no longer relevant. But with the advent of HTML5, new problems arose. WebRTC is a thorn in the side that also creates a communication channel for video streams between browsers. Additionally, a user can be fingerprinted using certain JavaScript functions that work with text, as we use different hardware, causing text rendering to occur differently for everyone. As practice shows, 90% of users have unique results. These functions include:
- measureText()
- getBoundingClientRect()
Last edited: