- Joined
- 26.12.23
- Messages
- 247
- Reaction score
- 13,406
- Points
- 93

? Carding Bites: 3DS/VBV Demystified Part 1 ?
Imagine this: you've got a new card, a good target and you're ready to score big. Then a wild 3DS prompt pops up and crushes your dreams faster than a bouncer spotting a fake ID. Sound familiar? Welcome to the bane of modern carding.

3D Secure or 3DS as we call it in the trenches has been our nemesis for years. But heres the thing - knowledge is power and were about to arm you with a whole lot of it.
In this two part guide were going to tear 3DS apart from the inside out. Part 1 will cover the basics history and general workings of 3DS. Part 2 will go even deeper into the technical side and show you how to test BINs and real-world scenarios.
Now let's get one thing straight: If you're here looking for a spoon-fed list of non-VBV BINs you're in the wrong fucking place. That's plastered all over Telegram and this forum already. We're not here to hold your hand and give you a magic list. Instead we're going to dive into the real meat - teach you how to fish for those golden BINs yourself.
So grab your drink of choice, tell your Telegram groups you're going dark for a bit and let's get into 3D Secure. Your future scores will thank you.
What the Hell is 3DS? A History Lesson You Didnt Ask For
Alright kids gather round, its time for a history lesson. While some dog carders are still scratching their heads over 3DS in 2024 like its some new tech, this shit's been around since 2001. Yeah, you heard that right: its old enough to drink in the States.

3D Secure or 3DS for those of us who can't be bothered with extra syllables stands for Three Domain Secure. It's not some fancy 3D graphics bullshit dsespite its name - it's three domains working together to make our lives harder:
Acquirer Domain: The merchant and their bank
Issuer Domain: The cardholder's bank
Interoperability Domain: The payment system that makes it all work (think Visa, Mastercard)
Back in the wild west days of e-commerce fraud was so rampant it makes today's carding scene look like a picnic. We're talking about 50% of disputed transactions at Visa Europe in 1998 coming from e-commerce. Merchants were getting reamed and card issuers were bleeding money faster than a dumbass getting slashed in a knife fight.
So in 2001 Visa decided to be the party pooper and rolled out 3DS. The idea was simple: add an extra layer of security to online transactions. No more of this "card number and you're good to go" bullshit. Now, cardholders had to jump through an extra hoop - usually enter a password - to prove they weren't some basement-dwelling fraudster.

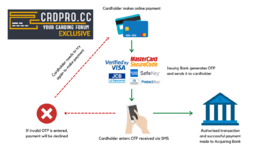
Why did merchants sign up for this pain in the ass? Two words: Liability Shift. With 3DS, if a transaction goes through and later turns out to be fraudulent, its the issuing bank's problem not the merchant. Sudenly merchants were rubbing their hands in glee over not eating chargebacks for breakfast lunch and dinner.
Enter Cardinal Commerce. These clever buggers saw an opportunity in this 3DS mess and positioned themselves as the middlemen of middlemen. They're like the bouncers of the digital payment world, contracted by banks to do the dirty work of 3DS authentication.

Why would banks use these third-party providers? Simple. Implementing and maintaining 3DS is a pain. It's like trying to teach your grandma to use TikTok - technically possible, but why bother when you can pay someone else to deal with the headache? Companies like Cardinal Commerce do this stuff, offering banks a solution to their problems. This is the reason why during 3DS you will, more often than not, see CardinalCommerce in the HTTP logs.
3DS 1.0 was as user-friendly as a cactus dildo. Cardholders were forgetting passwords, abandoning carts and generally hating life. Conversion rates plummeted and merchants were stuck between a rock and a hard place - fraud protection or sales?
Then we got 3DS 2.0 in 2016. This update was supposed to make the process smoother than a well-oiled... well, you get the idea. Instead of clunky passwords it uses risk-based authentication. Now the system analyses over 100 data points in the background to decide if it needs to bother the cardholder for extra verification.

Today 3DS is managed by EMVCo, a consortium that sounds like a supervillain organisation but is actually run by EuroPay, Mastercard and Visa. It's become the industry standard, with every major card network on board.
From fraud-fighting hero to conversion-killing villain and back again. It has been blocking carders for over 20 years and its not going away. But dont worry - where theres a will (and a bunch of clever fuckers like us) theres always a way.
How does it work?
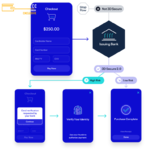
When someone pays online, here's what happens behind the scenes:
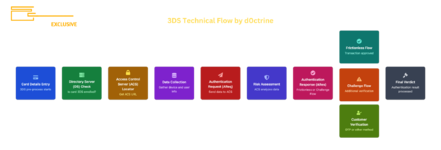
Card Details Entry: As soon as those digits hit the merchant's site, the 3DS pre-process starts.
Directory Server (DS) Check: The merchant's 3DS server pings the DS, basically asking, "Is this card part of the 3DS club?"
Access Control Server (ACS) Locator: If the card's enrolled, the DS spits back the URL for the card's ACS - think of it as the card's bouncer.
Data Collection: Now the 3DS server goes full-on NSA, collecting everything from device info to the customer's zodiac sign.
Authentication Request (AReq): All this juicy data gets bundled up and sent to the ACS.
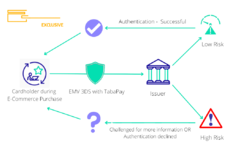
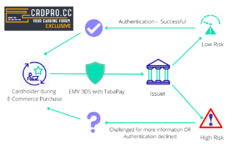
Risk Assessment: The ACS runs this data through its bullshit detector.
Authentication Response (ARes): Based on its assessment, the ACS decides whether to:
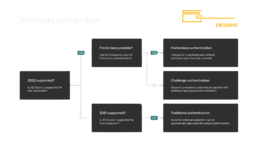
a) Greenlight the transaction (Frictionless Flow)
b) Throw up a challenge (Challenge Flow)
Challenge Flow (if triggered): Customer has to prove they're legit, maybe with a one-time password or by sacrificing their firstborn.
Final Verdict: The 3DS server gets the authentication result. If it's a thumbs up, the payment goes through.

The 3DS Trifecta: Challenge, Frictionless, and No-Show
Now, let's break it down:

1. Challenge Flow:
• What it looks like: A popup asking for extra verification.
• Methods: OTP, biometrics, security questions.
• For carders: Usually where your operation goes tits up.
2. Frictionless Flow:• What it looks like: Nothing. User doesn't even know 3DS happened.
• Behind the scenes: ACS gives you a pass based on risk assessment.
• For carders: This is what you're aiming for. Cards that are called AUTOSKIP goes through this easily.
3. No 3DS:• What it looks like: Standard checkout without extra steps.
• Behind the scenes: Transaction goes straight to authorization.
• For carders: The holy grail. Terms like NONVBV come into play here.
Remember: 3DS isn't just triggered by one entity. It's a two-headed beast, with both the issuing bank and the payment processor ready to rain on your parade.
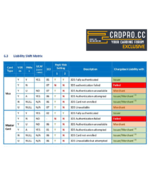
Bank-Side Triggers:
The issuing bank's trigger system is like a paranoid bouncer with a very specific shit list:
Transaction Amount: Sudden big-ticket purchases or amounts that don't fit the cardholder's usual spending.
Geo-location: Transactions from countries the cardholder's never set foot in.
Merchant Category: Some high-risk categories always trigger 3DS, like online gambling or adult entertainment.
Velocity: Rapid-fire transactions that make it look like the card's being passed around like a joint.
New Merchant: First-time transactions with a merchant the cardholder's never used before.
Processor-Side Triggers:
This is where those written in my AI Fraud Systems come into play, analyzing a fuck-ton of data points:
Device Fingerprint: The unique digital scent of your device and browser.
Behavioral Biometrics: How you type, move your mouse - basically your digital body language.
Historical Patterns: Previous transactions linked to the card, email or device.
Network Analysis: Connections between different transactions and accounts, like a digital spider web.
The Trigger Interplay:
Here's the thing - the bank and processor don't always see eye to eye. This creates a matrix of possible outcomes:
Clean Pass: You slip by both. Good job, you sneaky devil.
Bank 3DS: The bank gets spooked and triggers 3DS, processor be damned.
Processor 3DS: The processor's AI smells a rat and calls for 3DS.
Double Whammy: Both flag you. At this point you might as well be wearing an "I'm a fraudster" tee shirt.
Advanced Fuckery:
Selective 3DS: Some merchants only use 3DS above certain amounts. Scope your targets like a sniper.
Soft Decline Exploitation: Some issuers use "soft declines" instead of 3DS. This can be exploited with the right retry strategy.
3DS Downgrade: In rare cases you can force a 3DS1 authentication instead of 3DS2, more vulnerabilities open up.
NONVBV: Some banks don't support 3DS at all. In the carder world these are called NONVBV. Without 3DS these transactions are a walk in the park.
AUTOSKIP: Some banks implement a proxy 3DS that always pushes you through a frictionless flow—no challenge, just a green light. Carders and sellers know these as AUTOSKIP. Find these and you're set.
Conclusion: 3DS - Know Your Enemy
We've gone deep into the 3DS rabbit hole and if your head isn't spinning you weren't paying attention.

So let's recap:
3DS isn't new - it's been blocking carders since time immemorial.
It's a three-way tango between the Acquirer, Issuer and Interoperability domains.
The liability shift is why merchants cream their jeans over 3DS.
There are three possible outcomes: Challenge Flow, Frictionless Flow and No 3DS.
Both banks and processors can trigger 3DS, it's a complex web of fuckery.
We've only just begun. In Part 2 of this guide we'll go even deeper into the technical side of 3DS. We'll show you:
What SCA (Strong Customer Authentication) is
How merchants see these transactions
How to test BINs for 3DS support
Real-world examples with actual shops (because theory is great but practice pays the bills)
We'll also cover advanced techniques like Selective 3DS, Soft Decline Exploitation and the holy grail of NONVBV and AUTOSKIP cards.
Remember, understanding 3DS isn't just about bypassing it - it's about knowing when and why it's triggered in the first place. It's the difference between playing checkers and 4D chess in the carding world.
So until next time, keep your wits about you and your cards sharper. And for fuck's sake don't go plugging random BINs into every shop you see. That's amateur hour shit and you're better than that.
Class dismissed, you lovely degenerates. See you in Part 2 where we'll turn this into cold hard cash.
d0ctrine out.
Attachments
Last edited: