- Joined
- 31.10.19
- Messages
- 1,178
- Reaction score
- 3,115
- Points
- 113
Everything connected to the network can be found - if there is a desire and the right tool. Scanners like Shodan, ZoomEye, Netlas, Censys, FOFA and Criminal IP have long transcended the realm of "search engines for hackers" and have become workhorses for cybersecurity specialists, Red Teams, SOC analysts and OSINT enthusiasts. They allow users to literally peek into the "technical underbelly" of the internet: finding vulnerable cameras, forgotten databases, unauthorized test servers and industrial equipment accidentally exposed to the outside. This article provides a comparison of six of the most popular and useful open host search engines. It examines the architectural features, query syntax, availability of functions and capabilities of each platform -including APIs, integrations with other solutions, alert systems and searches by certificates, images, etc. Special attention is given to practical application examples and the relevance of the data. This is the first part of a series dedicated to comparative reviews. It thoroughly explores the capabilities of Shodan and ZoomEye. To provide an immediate overview, below is a summary table with the key characteristics of each platform:
As can be seen, each platform has its own specifics. Next, we will move on to a detailed review of each, including usage examples.
Shodan is the most well-known search engine for internet-connected devices, launched around 2009. Its scanners continuously traverse the entire IPv4 address space (and partially IPv6) to collect data on open ports and services. Over more than a decade, Shodan has amassed a vast database: by some estimates, it processes information on approximately 500 million devices and services monthly. Its geographical coverage is global; on the Shodan device map, the United States and Europe traditionally lead, along with major Asian countries (China, South Korea, India, etc), which are regions with the highest number of internet-connected nodes.
Initially, Shodan scanned only popular ports (80, 443, 21, 22, 23, 25, 3389, etc), but in recent years, the list has significantly expanded - by 2024, Shodan regularly checks around 1237 ports. The main focus is on the most common ones: web (HTTP/HTTPS on 80, 443, as well as 8080, 8443), FTP (21), SSH (22), Telnet (23), SNMP (161), SMTP (25), RDP (3389), SIP (5060), etc. Less popular ports are also included in the scanning, albeit with lower frequency. The frequency of Shodan's updates depends on the demand for the port: for example, port 80 is checked daily, while rare ports may be scanned every few weeks. Shodan retains a so-called banner for each found service - an identifier of the service or protocol along with accompanying information. The host record captures all discovered open ports and received responses. For example, for a web server, Shodan saves HTTP headers (Server, Date, Content-Type, etc.) and part of the HTML code of the page; for a TLS service, it saves the certificate; for SSH, it saves protocol parameters (algorithms, keys). Metadata is also automatically assigned: geolocation (country, city) and organization are determined by IP (GeoIP and WHOIS ASN). Some devices are categorized by Shodan (tags): for example, industrial control system, webcam, router, database, etc. - but the tag: filter can only be used by corporate subscribers. An important feature of Shodan is that it automatically attempts to match the received banners with known vulnerabilities: a vuln: filter by CVE is available for subscribers. For example, the query vuln:CVE-2019-19781 countryDE will find all vulnerable Citrix gateways in Germany in Shodan and the corresponding CVEs will be indicated next to the banner in the results list. Thus, Shodan not only shows which service is responding on the port but also immediately warns about known vulnerable versions.
The Shodan web interface is intuitive. The search bar supports both simple keywords and special filters. By default, a query without filters attempts to find the word in the content of any banners. Popular filters include country, city, autonomous system, organization, domain name, IP or network, port, product name, etc.
It's also worth noting Shodan Images, which is a sort of gallery of screenshots of device interfaces (cameras, remote desktops, etc.) captured by Shodan; access to it's also restricted to paid accounts. Search results are displayed as a list of IP addresses with a brief summary: country, organization, open ports and a snippet of the banner. By clicking on a result, one can see complete information about the node: all collected banners, metadata, possible domain names, known vulnerabilities (CVE) and geolocation on a map. For large clients, Shodan also provides additional interfaces, such as Shodan Maps (a cartographic view of devices on a world map) and Shodan Trends (statistics on the prevalence of certain technologies over time). These features are available on corporate plans.
Without registration, Shodan allows only a few trial searches. A free account provides basic access: web search displaying the first 2-3 pages of results and a limited API. For extended use, a one-time Shodan Membership subscription is offered for $49, which permanently increases limits - up to 1 million search results and a significantly higher daily API request limit. This is a one-time payment that doesn't require a subscription fee - many enthusiasts find this sufficient for their needs. For professional use, there are monthly plans: Freelancer ($69/month), Small Business ($359/month) and so on, up to corporate plans. These provide credits for an even larger number of requests (from 10,000 to unlimited), include the ability to on-demand scan their own IPs (Shodan Scanner) and access features like Shodan Monitor (continuous monitoring of specified networks) - for example, on the business plan, one can monitor up to 16 IP addresses in real-time, while on the corporate plan, up to a /16 network. Overall, Shodan's pricing policy is aimed at different categories: from students and researchers (one-time $49) to large companies (tens of thousands of dollars for full API data access).
Shodan is widely used to find vulnerable or misconfigured services. A classic case is the discovery of open databases or storage. For example, the query "MongoDB Server Information" port:27017 -authentication instantly finds hundreds of unsecured MongoDB instances worldwide (without a password) - such a data leak was once uncovered by journalists using Shodan.
Another example is the search for industrial SCADA/ICS controllers or urban systems: the filter product:"Niagara AX" yields control panels for Tridium Niagara building systems (some of which may be unsecured). For bug bounty and red teaming needs, Shodan is also indispensable; one can find surveillance cameras with default passwords (by the string www-authenticate: Basic realm="), printers with open control panels ("Server: HP HTTP/1.1"), or vulnerable VMware vCenter (searching by unique headers and CVEs). The flexibility of Shodan's query language allows for combining conditions to obtain very precise selections. For instance, a specialist can create a query that returns all Windows servers in a specific country with open RDP and a particular vulnerability - and Shodan will find such nodes in seconds, whereas manual scanning would take days. Shodan actively integrates with external tools. There are Shodan plugins for Nmap, Metasploit, Maltego and browser extensions (the Shodan plugin for Firefox highlights information about the current site). The official CLI utility (shodan in Python) allows for searching and retrieving data from the terminal. Additionally, Shodan maintains an open project called InternetDB - a free API with brief information about IP addresses (e.g, which ports are open) for cases where only a quick response is needed and full search is excessive. All these integrations make Shodan a sort of "platform" for internet scanning. It's no wonder that Shodan is mentioned in most OSINT reconnaissance and pentesting methodologies as the first tool for quickly assessing an organization's attack surface.

*the most popular queries are displayed, including applications for AI, control panels and open web interfaces.
The service allows for searching through hosts and web content.
ZoomEye is the Chinese equivalent of Shodan, launched by Knownsec around 2013. The service is positioned as a "global cyber scanning system" and was initially aimed at the local community (the interface was in Chinese), but is now also available in English. ZoomEye's approach differs slightly: it divides the search into two types: Host Search and Web Search. Host Search is similar to Shodan (searching for devices by IP and their ports), while Web Search allows users to search websites by page content. This means that ZoomEye indexes not only the hosts themselves but also the web content (HTML) of sites, bringing it closer to traditional web search engines, albeit for a limited set of discovered sites.
ZoomEye claims to cover the entire IPv4 and a significant portion of active IPv6 addresses, as well as domain names. The total number of indexed devices is comparable to Shodan (in the hundreds of millions), but there is a nuance: ZoomEye retains historical data on all discovered hosts. The interface by default shows the total number of results over the entire observation period, which may make ZoomEye appear to yield significantly more results than Shodan at first glance. For a more accurate comparison of current devices, it's recommended to use a time filter (e.g, Past Year). ZoomEye's port scanning is very extensive: experimental estimates suggest that the service checks around 3,828 ports - almost all significant ports up to 65,535. This is substantially more than Shodan (1,237 ports). However, like Shodan, ZoomEye more frequently updates popular ports (80, 443, etc), while exotic ports may be scanned less often (every few weeks or months). Nevertheless, this broad coverage means that ZoomEye sometimes finds services on rare ports that may have been missed by other scanners. An interesting feature is on-demand scanning: an authorized ZoomEye user can manually request immediate scanning of a specific IP or domain to update the data. This is convenient if one needs to check whether a vulnerability on a known host has been closed - there's no need to wait for a scheduled scan; the system will scan the target immediately.
The query syntax of ZoomEye is largely similar to Shodan but has its own keywords. For example, app="Apache httpd" && ver="2.4.33" && country="US" in Host Search mode will find all Apache 2.4.33 instances in the United States.
Popular ZoomEye filters include: app (application or server name), ver (software version), port (port number), service (protocol/service - list corresponds to names from nmap), os (operating system), hostname (domain name found in the banner), site (domain in Web Search mode for searching website content), headers (search for a fragment in HTTP headers) and others. In Web Search mode, filters such as title (page title), keywords (keywords in text) and desc (site description) are available. The ZoomEye interface is available in both English and Chinese. In Host Search mode, results are presented as a list of IPs with brief data: open ports, services, organization and country. In Web Search mode, a list of URLs with snippets of page text is displayed. An interesting detail is that each search result in ZoomEye has a "Vulnerability" tab, which is unique for such services. This tab lists popular vulnerabilities relevant to the current query or category of devices. In fact, ZoomEye is integrated with a major Chinese exploit database, Seebug. Users can click on a specific vulnerability from the list and ZoomEye will automatically generate a query showing all hosts potentially vulnerable to it. This allows for a quick transition from vulnerability information to specific targets, significantly speeding up threat analysis. This feature is especially useful for reactive searches - when a new vulnerability is released, one can immediately find all vulnerable systems.
ZoomEye provides free access with some limitations. After registration, a free user can view up to 10,000 results per month and monitor up to 50 IP addresses. This is sufficient for familiarization, but for serious work, a subscription is required. Paid plans for ZoomEye start at around $70 per month, which provides a quota of approximately 30,000 results/month and monitoring of 256 IPs. More expensive plans expand these limits. However, there is an important limitation: even on paid accounts, ZoomEye doesn't allow exporting more than a certain threshold of results (for example, one cannot export a million records at once; there is a limit in the interface). In this regard, FOFA offers a more advantageous option (discussed later). Overall, ZoomEye's pricing policy is aimed at professionals within China, many of whom use it in conjunction with Knownsec services (such as the vulnerability discussion platform Seebug and the Pocsuite exploit framework). For external specialists, ZoomEye is valuable as an additional resource, especially when considering data from the Asian region.
In addition to its general function of searching for vulnerable services, ZoomEye is popular for tasks related to finding devices in China and Asia. For example, if Shodan might miss a specific Chinese IoT device or web application, ZoomEye/FOFA is likely to detect it. ZoomEye is also widely used for searching ICS/SCADA systems: it has a filter for device types (for instance, one can select SCADA and obtain a list of known vulnerable control systems). ZoomEye sometimes finds more open RDP or SMB services in certain networks than Shodan, thanks to its less frequent but still broad scanning of ports 3389, 445 and others. Another use case is bug bounty hunting in Asia: when testing the security of Asian companies, ZoomEye helps discover their external hosts, as it better indexes local resources (for example, .cn domains, Chinese cloud providers). Overall, it's advisable to use ZoomEye in conjunction with Shodan: first, search in Shodan (as it's more current) and then run the same queries in ZoomEye - there's a chance to uncover historical or rare targets.
Today, Shodan and ZoomEye represent two of the primary platforms used in the practice of cyber reconnaissance and infrastructure protection. Each offers a unique approach to indexing open hosts: Shodan focuses on relevance and a rich ecosystem of integrations, while ZoomEye stands out with its extensive port selection, historical coverage and built-in linkage to the Seebug vulnerability database. Practical experience shows that these tools demonstrate the greatest effectiveness when used together. Shodan provides quick access to fresh data, while ZoomEye allows for the identification of rare or long-exposed targets, including those in the Asian segment of the internet.
| Platform | Launch | Port Coverage | Free Version | Paid Plans | Unique Features |
|---|---|---|---|---|---|
| Shodan | 2009 | ~1237 ports (IPv4) | Yes (very limited) | $49 one-time (Lifetime), then from $69/month | IP monitoring (Shodan Monitor), vulnerability search (vuln: filter), integration with many tools |
| ZoomEye | 2013 | ~3828 ports (IPv4/IPv6) | Yes (up to 10k results/month) | From ~$70/month (30k results) | Two search modes (Host/Web), vulnerability tab (Seebug integration), on-demand target scanning |
| Censys | 2015 | All 65k ports (IPv4, partially IPv6) | Yes (250+ queries, limited fields) | Enterprise (expensive, custom) | Structured data on services, separate search for certificates, strong API for research |
| FOFA | 2017 | >1200 ports (IPv4, partially IPv6) | Yes (only 100 results) | Personal ~$100/year (10k results/query), higher VIP plans | Content search (body), favicon search (hash), alerts for new results |
| Netlas | 2022 | 146 ports (public) / ~1300 (private) | Yes (Community API, ~50 queries/day) | Freelancer $49/month, Business $249/month | Indexes domains + DNS, regular data updates, streaming API, integrations (browser, Maltego) |
| Criminal IP | 2022 | ~65535 ports (IPv4, honeypots, passive analysis) | Yes (limited credits) | Basic ~$29/month and up | IP risk assessment (IP Risk Score), image search (OCR), detection of proxies/VPNs/scanners, domain reports (URL scanner) |
As can be seen, each platform has its own specifics. Next, we will move on to a detailed review of each, including usage examples.
Shodan
Shodan
General Characteristics
Shodan is the most well-known search engine for internet-connected devices, launched around 2009. Its scanners continuously traverse the entire IPv4 address space (and partially IPv6) to collect data on open ports and services. Over more than a decade, Shodan has amassed a vast database: by some estimates, it processes information on approximately 500 million devices and services monthly. Its geographical coverage is global; on the Shodan device map, the United States and Europe traditionally lead, along with major Asian countries (China, South Korea, India, etc), which are regions with the highest number of internet-connected nodes.
Depth of Indexing
Initially, Shodan scanned only popular ports (80, 443, 21, 22, 23, 25, 3389, etc), but in recent years, the list has significantly expanded - by 2024, Shodan regularly checks around 1237 ports. The main focus is on the most common ones: web (HTTP/HTTPS on 80, 443, as well as 8080, 8443), FTP (21), SSH (22), Telnet (23), SNMP (161), SMTP (25), RDP (3389), SIP (5060), etc. Less popular ports are also included in the scanning, albeit with lower frequency. The frequency of Shodan's updates depends on the demand for the port: for example, port 80 is checked daily, while rare ports may be scanned every few weeks. Shodan retains a so-called banner for each found service - an identifier of the service or protocol along with accompanying information. The host record captures all discovered open ports and received responses. For example, for a web server, Shodan saves HTTP headers (Server, Date, Content-Type, etc.) and part of the HTML code of the page; for a TLS service, it saves the certificate; for SSH, it saves protocol parameters (algorithms, keys). Metadata is also automatically assigned: geolocation (country, city) and organization are determined by IP (GeoIP and WHOIS ASN). Some devices are categorized by Shodan (tags): for example, industrial control system, webcam, router, database, etc. - but the tag: filter can only be used by corporate subscribers. An important feature of Shodan is that it automatically attempts to match the received banners with known vulnerabilities: a vuln: filter by CVE is available for subscribers. For example, the query vuln:CVE-2019-19781 countryDE will find all vulnerable Citrix gateways in Germany in Shodan and the corresponding CVEs will be indicated next to the banner in the results list. Thus, Shodan not only shows which service is responding on the port but also immediately warns about known vulnerable versions.
Interface and Search
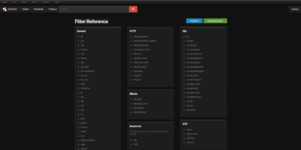
The Shodan web interface is intuitive. The search bar supports both simple keywords and special filters. By default, a query without filters attempts to find the word in the content of any banners. Popular filters include country, city, autonomous system, organization, domain name, IP or network, port, product name, etc.

*list of supported Shodan filters, grouped by categories (SSL, HTTP, Restricted, etc.). These filters help refine queries when searching through banners.
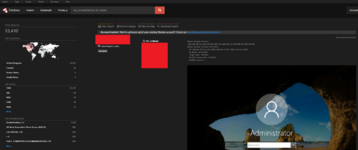
For example, the query country:RU port:22 will display SSH servers in Russia, while org:"Energy" will show devices belonging to organizations with the name Energy. Shodan also recognizes various protocol fields: one can search by the content of HTTP headers (http.title, http.html), fields of SSL certificates (ssl.cert.subject), device type (device) and even the presence of a remote screen screenshot (has_screenshot:true). For instance, has_screenshot:true city:London will show systems (usually VNC/RDP) for which Shodan has taken screenshots in London.

*screenshot of a RDP automatically captured by Shodan. Such images allow for an instant assessment of exposed interfaces - from server panels to Windows login screens.
It's also worth noting Shodan Images, which is a sort of gallery of screenshots of device interfaces (cameras, remote desktops, etc.) captured by Shodan; access to it's also restricted to paid accounts. Search results are displayed as a list of IP addresses with a brief summary: country, organization, open ports and a snippet of the banner. By clicking on a result, one can see complete information about the node: all collected banners, metadata, possible domain names, known vulnerabilities (CVE) and geolocation on a map. For large clients, Shodan also provides additional interfaces, such as Shodan Maps (a cartographic view of devices on a world map) and Shodan Trends (statistics on the prevalence of certain technologies over time). These features are available on corporate plans.
Availability and Pricing
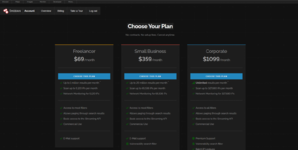
Without registration, Shodan allows only a few trial searches. A free account provides basic access: web search displaying the first 2-3 pages of results and a limited API. For extended use, a one-time Shodan Membership subscription is offered for $49, which permanently increases limits - up to 1 million search results and a significantly higher daily API request limit. This is a one-time payment that doesn't require a subscription fee - many enthusiasts find this sufficient for their needs. For professional use, there are monthly plans: Freelancer ($69/month), Small Business ($359/month) and so on, up to corporate plans. These provide credits for an even larger number of requests (from 10,000 to unlimited), include the ability to on-demand scan their own IPs (Shodan Scanner) and access features like Shodan Monitor (continuous monitoring of specified networks) - for example, on the business plan, one can monitor up to 16 IP addresses in real-time, while on the corporate plan, up to a /16 network. Overall, Shodan's pricing policy is aimed at different categories: from students and researchers (one-time $49) to large companies (tens of thousands of dollars for full API data access).
Usage Examples
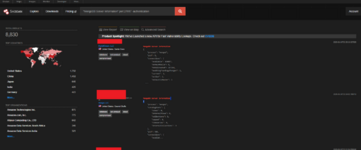
Shodan is widely used to find vulnerable or misconfigured services. A classic case is the discovery of open databases or storage. For example, the query "MongoDB Server Information" port:27017 -authentication instantly finds hundreds of unsecured MongoDB instances worldwide (without a password) - such a data leak was once uncovered by journalists using Shodan.

*searching in Shodan with the filter "MongoDB Server Information" port:27017 -authentication reveals thousands of MongoDB instances with open access..
Another example is the search for industrial SCADA/ICS controllers or urban systems: the filter product:"Niagara AX" yields control panels for Tridium Niagara building systems (some of which may be unsecured). For bug bounty and red teaming needs, Shodan is also indispensable; one can find surveillance cameras with default passwords (by the string www-authenticate: Basic realm="), printers with open control panels ("Server: HP HTTP/1.1"), or vulnerable VMware vCenter (searching by unique headers and CVEs). The flexibility of Shodan's query language allows for combining conditions to obtain very precise selections. For instance, a specialist can create a query that returns all Windows servers in a specific country with open RDP and a particular vulnerability - and Shodan will find such nodes in seconds, whereas manual scanning would take days. Shodan actively integrates with external tools. There are Shodan plugins for Nmap, Metasploit, Maltego and browser extensions (the Shodan plugin for Firefox highlights information about the current site). The official CLI utility (shodan in Python) allows for searching and retrieving data from the terminal. Additionally, Shodan maintains an open project called InternetDB - a free API with brief information about IP addresses (e.g, which ports are open) for cases where only a quick response is needed and full search is excessive. All these integrations make Shodan a sort of "platform" for internet scanning. It's no wonder that Shodan is mentioned in most OSINT reconnaissance and pentesting methodologies as the first tool for quickly assessing an organization's attack surface.
ZoomEye

*the most popular queries are displayed, including applications for AI, control panels and open web interfaces.
The service allows for searching through hosts and web content.
General Characteristics
ZoomEye is the Chinese equivalent of Shodan, launched by Knownsec around 2013. The service is positioned as a "global cyber scanning system" and was initially aimed at the local community (the interface was in Chinese), but is now also available in English. ZoomEye's approach differs slightly: it divides the search into two types: Host Search and Web Search. Host Search is similar to Shodan (searching for devices by IP and their ports), while Web Search allows users to search websites by page content. This means that ZoomEye indexes not only the hosts themselves but also the web content (HTML) of sites, bringing it closer to traditional web search engines, albeit for a limited set of discovered sites.
Depth of Indexing
ZoomEye claims to cover the entire IPv4 and a significant portion of active IPv6 addresses, as well as domain names. The total number of indexed devices is comparable to Shodan (in the hundreds of millions), but there is a nuance: ZoomEye retains historical data on all discovered hosts. The interface by default shows the total number of results over the entire observation period, which may make ZoomEye appear to yield significantly more results than Shodan at first glance. For a more accurate comparison of current devices, it's recommended to use a time filter (e.g, Past Year). ZoomEye's port scanning is very extensive: experimental estimates suggest that the service checks around 3,828 ports - almost all significant ports up to 65,535. This is substantially more than Shodan (1,237 ports). However, like Shodan, ZoomEye more frequently updates popular ports (80, 443, etc), while exotic ports may be scanned less often (every few weeks or months). Nevertheless, this broad coverage means that ZoomEye sometimes finds services on rare ports that may have been missed by other scanners. An interesting feature is on-demand scanning: an authorized ZoomEye user can manually request immediate scanning of a specific IP or domain to update the data. This is convenient if one needs to check whether a vulnerability on a known host has been closed - there's no need to wait for a scheduled scan; the system will scan the target immediately.
Search Language and Interface
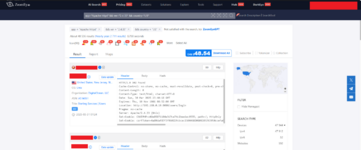
The query syntax of ZoomEye is largely similar to Shodan but has its own keywords. For example, app="Apache httpd" && ver="2.4.33" && country="US" in Host Search mode will find all Apache 2.4.33 instances in the United States.

*the results display HTTP headers, IP addresses, organizations, geographical locations and a map.
Popular ZoomEye filters include: app (application or server name), ver (software version), port (port number), service (protocol/service - list corresponds to names from nmap), os (operating system), hostname (domain name found in the banner), site (domain in Web Search mode for searching website content), headers (search for a fragment in HTTP headers) and others. In Web Search mode, filters such as title (page title), keywords (keywords in text) and desc (site description) are available. The ZoomEye interface is available in both English and Chinese. In Host Search mode, results are presented as a list of IPs with brief data: open ports, services, organization and country. In Web Search mode, a list of URLs with snippets of page text is displayed. An interesting detail is that each search result in ZoomEye has a "Vulnerability" tab, which is unique for such services. This tab lists popular vulnerabilities relevant to the current query or category of devices. In fact, ZoomEye is integrated with a major Chinese exploit database, Seebug. Users can click on a specific vulnerability from the list and ZoomEye will automatically generate a query showing all hosts potentially vulnerable to it. This allows for a quick transition from vulnerability information to specific targets, significantly speeding up threat analysis. This feature is especially useful for reactive searches - when a new vulnerability is released, one can immediately find all vulnerable systems.
Availability and Pricing
ZoomEye provides free access with some limitations. After registration, a free user can view up to 10,000 results per month and monitor up to 50 IP addresses. This is sufficient for familiarization, but for serious work, a subscription is required. Paid plans for ZoomEye start at around $70 per month, which provides a quota of approximately 30,000 results/month and monitoring of 256 IPs. More expensive plans expand these limits. However, there is an important limitation: even on paid accounts, ZoomEye doesn't allow exporting more than a certain threshold of results (for example, one cannot export a million records at once; there is a limit in the interface). In this regard, FOFA offers a more advantageous option (discussed later). Overall, ZoomEye's pricing policy is aimed at professionals within China, many of whom use it in conjunction with Knownsec services (such as the vulnerability discussion platform Seebug and the Pocsuite exploit framework). For external specialists, ZoomEye is valuable as an additional resource, especially when considering data from the Asian region.
Usage Examples
In addition to its general function of searching for vulnerable services, ZoomEye is popular for tasks related to finding devices in China and Asia. For example, if Shodan might miss a specific Chinese IoT device or web application, ZoomEye/FOFA is likely to detect it. ZoomEye is also widely used for searching ICS/SCADA systems: it has a filter for device types (for instance, one can select SCADA and obtain a list of known vulnerable control systems). ZoomEye sometimes finds more open RDP or SMB services in certain networks than Shodan, thanks to its less frequent but still broad scanning of ports 3389, 445 and others. Another use case is bug bounty hunting in Asia: when testing the security of Asian companies, ZoomEye helps discover their external hosts, as it better indexes local resources (for example, .cn domains, Chinese cloud providers). Overall, it's advisable to use ZoomEye in conjunction with Shodan: first, search in Shodan (as it's more current) and then run the same queries in ZoomEye - there's a chance to uncover historical or rare targets.
Conclusion
Conclusion
Today, Shodan and ZoomEye represent two of the primary platforms used in the practice of cyber reconnaissance and infrastructure protection. Each offers a unique approach to indexing open hosts: Shodan focuses on relevance and a rich ecosystem of integrations, while ZoomEye stands out with its extensive port selection, historical coverage and built-in linkage to the Seebug vulnerability database. Practical experience shows that these tools demonstrate the greatest effectiveness when used together. Shodan provides quick access to fresh data, while ZoomEye allows for the identification of rare or long-exposed targets, including those in the Asian segment of the internet.






