- Joined
- 31.10.19
- Messages
- 1,178
- Reaction score
- 3,115
- Points
- 113
In the second part of the comparative review, the analysis of leading internet scanners and OSINT platforms continues. This time, the focus is on Censys and FOFA - powerful tools, each offering unique approaches to collecting and structuring data about open services on the internet. The article examines the architecture of the platforms, query syntax, port coverage, capabilities for searching certificates and web page content, as well as real-world application examples.
Censys originated from an academic project at the University of Michigan (the creators of the ZMap utility) and has established itself since its launch in 2015 as a "benchmark" source of internet data for research and corporate use. Censys focuses on comprehensive scanning of the entire IPv4 and deep analytics of the collected data. Unlike Shodan, Censys has provided open datasets and APIs for researchers from the very beginning, earning a reputation as a reliable and transparent resource. Currently, Censys is a commercial service (with venture funding) offering both a free mode for the community and paid solutions for enterprises (including an Attack Surface Management platform).
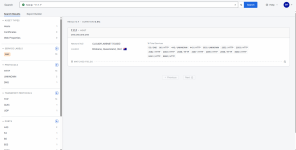
*a screenshot shows the result of searching for the IP address 1.1.1.1 through the Censys interface. It's evident that the host belongs to Cloudflare (AS13335) and is located in Brisbane, Australia. All discovered services and used ports are displayed, including HTTP, DNS and unknown. This presentation format allows for quick analysis of the activity of a specific IP address.
The main distinction of Censys is that it scans the entire IPv4 across all 65,535 ports! Yes, you heard that right: high-performance scanners (the same ZMap + zgrab2 combination) are used to attempt to poll every port on every address. However, in practice, Censys differentiates between the top 100 popular ports and the rest to avoid being overwhelmed by uninformative data. The most popular ports (web, mail, SSH, RDP, SMB, etc.) are updated daily, and some even several times a day. The remaining ~65k ports are scanned less frequently, approximately once every 1–7 days on a rotation basis. Thus, the average host in Censys is rescanned approximately every few days, but critical services on it will be updated almost daily. Censys also scans IPv6 - although the coverage is far from complete (it's unrealistic to iterate through 2^128 addresses), the service supports searching through a considerable number of active IPv6 nodes, especially servers with global addresses. Additionally, Censys pays special attention to TLS certificates: it maintains an index of all SSL/TLS certificates encountered on the internet (including those visible through Certificate Transparency logs). This means Censys effectively maintains two large databases: Hosts (nodes/services) and Certificates (certificates). Thanks to this, Censys can find, for example, all domains where a specific certificate is used or monitor the emergence of new self-signed certificates on IoT devices.
Since Censys originates from an academic environment, it collects maximally structured data. A record about a node is presented as a JSON object, which includes a services section - a list of all open services on the host with detailed descriptions of each. For HTTPS, this includes the full certificate and its parameters (algorithms, cipher suites, supported TLS versions); for SSH, it includes supported algorithms and keys; for databases, it includes the DBMS version and some configuration parameters, etc. Censys actively correlates data: for example, it identifies virtual hosts - if one IP serves multiple domains (through the SAN certificate fields or HTTP Host), those domains are also counted as separate records. This results in a very large total number of records in Censys. For instance, considering virtual hosts, Censys has over 1.4 billion records for HTTPS (port 443). However, for practical tasks, virtual duplicates are usually filtered out: when counting unique IPv4 addresses, Censys detects about 50 million hosts with web ports, ~21 million with SSH, ~24 million with Telnet/CWMP, etc. - figures close to Shodan. This indicates a high completeness of Censys's coverage: it's at least on par with Shodan in terms of the number of active IPv4 nodes and in terms of data (e.g, the presence of TLS), it surpasses it.
In 2022, Censys introduced a new query language - Censys Search Language, which unified the search for hosts and certificates. Previously, searches were conducted through separate interfaces (and APIs) for Hosts and Certificates; now, conditions for both can be combined in a single query. Queries in Censys can be made using simple string searches (similar to Shodan) or as logical expressions based on fields. For example, a simple query like "Apache httpd 2.4.X country:US" will find all banners for Apache 2.4.xx in the United States (string search for banners + country filter). However, the true power of Censys lies in structured searches through JSON fields. For instance, one could write: services.service_name: "HTTP" AND services.http.response.status_code: 200 AND location.country_code: "US" to find only hosts in the US that have HTTP open and where the web server responds with a status code of 200 (OK).
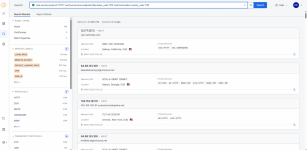
*a screenshot demonstrates an example of using an advanced query in Censys:
host.services.protocol:"HTTP" AND host.services.endpoints.http.status_code="200" AND location.country_code:"US".
Moreover, regular expressions and ranges are supported. For example, one can find all certificates issued to domains of the form *.gov.br (Brazilian government sites) that are expiring in less than 30 days - such queries have been described in researcher's blogs. The Censys interface (web portal) is quite minimalist: searching is done through a single line and results are displayed in tables or cards with the option to switch to detailed JSON. Many engineers find it more convenient to use the API directly or download complete datasets (Censys periodically publishes data dumps for research purposes).
Censys offers a free Community account, which is sufficient for basic queries. The limit in the free mode is 250 search queries per day (previously it was per month, but the model has changed) and access to most fields (except for very specific ones). The API is also available for free for these 250 requests/day with authentication. This volume is generally enough for one-time research and scripts. Commercial plans for Censys are aimed at large companies: exact prices are not disclosed (typically several thousand dollars per month and higher).
Censys is particularly favored by vulnerability researchers and academics. It's often used to measure the global prevalence of specific issues. For example, immediately after discovering a critical vulnerability (like Heartbleed or Log4Shell), experts use Censys to execute complex queries and count how many hosts on the internet remain vulnerable - these statistics are frequently cited in the media. Thanks to its certificate index, Censys allows for actions that are impossible in Shodan: for instance, finding all websites where the certificate contains the name of organization X (in the Subject or Issuer field). This aids in OSINT - identifying related domains of a company through certificates. Censys is also actively used for inventorying external assets: since it scans all ports, one can discover not only the usual 80/443 but also, say, a forgotten open RDP (3389) or an admin port of a custom application on port 8443, which Shodan might not have checked. Large companies regularly conduct audits of their networks using Censys. Overall, Censys is considered the "gold standard" in terms of data completeness. It answers the question "what exactly is running on this host?" in the most detailed manner. However, its use requires more experience due to the complexity of queries and the vast amount of information. Security engineers often combine Censys with Shodan: they perform a quick initial search on Shodan and then clarify details (service configurations, certificates, all ports) through Censys. This approach ensures both speed and depth.
FOFA (Eye of the Fox, Fingerprint Of All) is another representative of Chinese cyber scanners developed by Baimaohui, the organizer of the White Hat conference in China. Launched around 2017, FOFA gained recognition for its extensive coverage and ability to search through the content of banners and web pages. Many specialists in Russia discovered FOFA as an alternative to Shodan after several high-profile leaks were found specifically through FOFA, such as data leaks from unsecured Elasticsearch and Kibana instances that Shodan didn't index properly at the time. Initially focused on the Chinese internet segment, FOFA now features an English interface, similar to ZoomEye.
The name Fingerprint Of All reflects the service's goal of collecting "fingerprints" from everything available. FOFA scans the global IPv4 (and likely selectively IPv6, although exact details are not disclosed) similarly to Shodan. The number of ports is not explicitly stated, but it's known that FOFA indexes over 1200 ports, including rare ones. In tests conducted by the Netlas team, FOFA successfully covered the entire list of ports scanned by Shodan and even had its own additional list. Thus, in terms of port coverage, FOFA is comparable to Censys/ZoomEye (possibly not scanning all 65k, but more than sufficient for practical use). The update frequency for FOFA varies: more popular ports are scanned frequently (up to daily), while exotic ones may remain unupdated for several weeks. Developers have mentioned that priorities are set based on the prevalence of services. This means that FOFA, like Shodan, may have slightly outdated data on rare protocols but provides a fresh picture for the main ones. Overall, FOFA's coverage of unique nodes is comparable to Shodan (tens of millions of active hosts), although the service boasts "over 4 billion records" in its database (FOFA Reviews - 2025), likely counting all protocols, historical data, etc. FOFA also has a vast database of fingerprints - over 350,000 templates for identifying software and devices through banners (FOFA Reviews - 2025), successfully identifying many products, including those from Chinese manufacturers that are not always recognized in Shodan.
FOFA offers a rich query syntax, quite similar to Shodan but with its own specifics. Notably, filters can be written in both English and Chinese, catering to different audiences. For example, the query ip="8.8.8.8" is equivalent to ip.addr="8.8.8.8" and will find the specific IP.
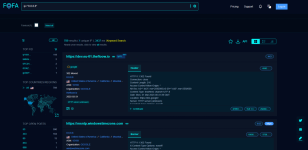
*a screenshot demonstrates the search results for the IP address 8.8.8.8 in the FOFA interface. The results display information about the services, banners, the owning organization (in this case - Google), as well as the protocols used (443/HTTPS).
You can set conditions using logical operators: FOFA uses && for AND, || for OR and ! for NOT (similar to programming language syntax). Grouping with parentheses is supported. Key filters in FOFA include: ip/ip.addr (IP address), port (port), domain (domain name from the certificate or banner), host (combined field: domain or IP: Port), title (HTML page title), banner (full text of the service banner), body (HTML body content), protocol (e.g, HTTP, SMB, RDP), status_code (HTTP response code), app (specific FOFA application/software name) and many more. FOFA is known for allowing searches through the content of web pages - essentially functioning like a search engine such as Google, but for devices that are usually not indexed. For example, the query body="password" will find all pages (in FOFA's index) where the word "password" appears. Similarly, header="Elastic" will find all hosts where the HTTP headers contain the word Elastic (often a sign of Elasticsearch). Searches can also be conducted by ASN (asn=), country (country=), OS (os=), certificate parameters (cert.subject= or cert.issuer=). Wildcards can be used: for instance, domain~=".edu.cn" will find all subdomains in the .edu.cn zone (using ~ as a contains operator). Overall, FOFA's language is slightly less strict than Censys's - it tolerates various filter writing styles and is user-friendly.
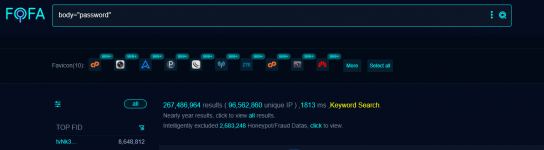
*a screenshot demonstrates the query body="password" in FOFA - one of the classic dork queries that allows users to find web pages containing fields for password input. This can be useful for identifying open login panels, vulnerable pages, or configuration interfaces.
FOFA has two web addresses: the Chinese fofa.so and the English fofa.info. After logging in, users can switch to the desired language. The interface is quite simple: a search bar and a dropdown list of filters. Results are displayed in a list format, where each line is either an IP: Port or domain: Port, along with a short snippet of the banner. An interesting detail is that FOFA by default shows not the entire banner but only the part where the search condition matches, highlighting the found string. This is convenient for text searches, but sometimes it may seem like there is little data - users need to click on the entry to see all fields in full. The host card presents all collected information: IP, ports, services, banners, domains, geolocation, etc. Paid users can export results in CSV/Excel format. Like ZoomEye, FOFA retains historical data: users can see when a host was first and last observed and how its banners changed over time.FOFA has a mobile application and even a desktop client (primarily aimed at Chinese users). The client includes a unique PoC accelerator - a store of exploits that allows users to immediately check found hosts for vulnerabilities (for example, by clicking and launching a ready-made exploit against a host). This is closely integrated with the Chinese ecosystem and is little used outside of China, but it demonstrates how advanced local tools aim to be.
A free FOFA account allows users to perform searches without request limits, but results are restricted to the first 100 entries. This means users will only see a small portion of the results before receiving a message stating "VIP required". For full functionality, a paid subscription is necessary. The pricing tiers include Personal VIP, Enterprise VIP and others. The basic personal account costs around $100 per year and allows viewing up to 10,000 results per query and using the API (with a limit, for example, of 1,000 API requests per day). Higher tiers (Corporate, Enterprise) increase limits - up to 100,000 results and unlimited API access for Enterprise. A significant advantage of FOFA over ZoomEye is the absence of artificial restrictions on scrolling through results: if you have VIP access, you can see all millions of results if they exist. In contrast, ZoomEye doesn't allow exporting more than a certain ceiling even with a paid account (for security reasons, to prevent downloading the entire database). Additionally, FOFA doesn't restrict queries on Chinese addresses: it is known that ZoomEye may hide some results related to critical infrastructure in China for political reasons, while FOFA is more open.
FOFA has several "features" that outpace its Western competitors. For instance, FOFA was one of the first to implement search by website icon (favicon hash). Users can upload a favicon.ico file in the interface and the service will find all hosts with the same icon hash - extremely useful for identifying similar web applications (e.g, admin panels of a specific product). Shodan later added such a function (http.favicon.hash), but FOFA was the pioneer. Another feature is the alerts system: users can save any search query and enable monitoring, allowing FOFA to send notifications when new results matching that query appear. This effectively serves as a tool for tracking one's resources or the emergence of new vulnerable devices based on specified criteria. FOFA is also developing a knowledge library (FOFA Library) - a section where articles and use cases are published (mostly in Chinese). For example, cases of mass scanning of government websites or searching for specific vulnerable devices on the internet have been discussed there, helping new users learn. FOFA also offers integrations: there is a plugin for BurpSuite (allowing users to search for exposed subdomains from the Burp interface), modules for Nmap, plugins for radiographic analysis (Radare) and more. The community around FOFA actively shares scripts and fingerprints.
FOFA is often preferred for searching for information that Shodan does not find. Primarily, this includes textual content on pages. For example, if you need to find all web interfaces of devices where a specific phrase appears on the page - Shodan will not help with banners, but FOFA will handle the query body="phrase". This has been used to find leaks of confidential data on forgotten pages, identifying interfaces with error messages containing keywords (e.g, "SQL error"). FOFA is also more useful for searching devices in the Asian internet segment: it better recognizes equipment from local brands, has a more complete database of Chinese ASNs and is actively used by local researchers. Therefore, if something appears in Chinese networks, it almost immediately gets indexed by FOFA. For OSINT on Chinese companies, FOFA is a must-have tool, while Shodan may miss parts of the infrastructure. Of course, FOFA cannot completely replace Shodan - its index also has gaps and the data refresh rate is somewhat inferior (on less popular nodes). Therefore, professionals often use them in tandem.
Censys and FOFA represent two completely different approaches to the problem of internet inventory. Censys maintains academic rigor and structure, providing highly accurate data with a high degree of detail, making it ideal for analytics, inventory,and vulnerability research. FOFA, on the other hand, emphasizes the breadth of coverage, flexibility of query language and content search capabilities - an indispensable function for OSINT and leak detection. Both platforms complement each other excellently. Using them in tandem allows users to address both monitoring tasks and OSINT, bug bounty and the search for specific assets on the internet. In the next part of the review, we will explore newer but actively developing solutions: Netlas and Criminal IP, which offer interesting approaches to searching, visualizing and analyzing digital footprints.
Censys
Censys
General Overview
Censys originated from an academic project at the University of Michigan (the creators of the ZMap utility) and has established itself since its launch in 2015 as a "benchmark" source of internet data for research and corporate use. Censys focuses on comprehensive scanning of the entire IPv4 and deep analytics of the collected data. Unlike Shodan, Censys has provided open datasets and APIs for researchers from the very beginning, earning a reputation as a reliable and transparent resource. Currently, Censys is a commercial service (with venture funding) offering both a free mode for the community and paid solutions for enterprises (including an Attack Surface Management platform).

*a screenshot shows the result of searching for the IP address 1.1.1.1 through the Censys interface. It's evident that the host belongs to Cloudflare (AS13335) and is located in Brisbane, Australia. All discovered services and used ports are displayed, including HTTP, DNS and unknown. This presentation format allows for quick analysis of the activity of a specific IP address.
Depth of Indexing
The main distinction of Censys is that it scans the entire IPv4 across all 65,535 ports! Yes, you heard that right: high-performance scanners (the same ZMap + zgrab2 combination) are used to attempt to poll every port on every address. However, in practice, Censys differentiates between the top 100 popular ports and the rest to avoid being overwhelmed by uninformative data. The most popular ports (web, mail, SSH, RDP, SMB, etc.) are updated daily, and some even several times a day. The remaining ~65k ports are scanned less frequently, approximately once every 1–7 days on a rotation basis. Thus, the average host in Censys is rescanned approximately every few days, but critical services on it will be updated almost daily. Censys also scans IPv6 - although the coverage is far from complete (it's unrealistic to iterate through 2^128 addresses), the service supports searching through a considerable number of active IPv6 nodes, especially servers with global addresses. Additionally, Censys pays special attention to TLS certificates: it maintains an index of all SSL/TLS certificates encountered on the internet (including those visible through Certificate Transparency logs). This means Censys effectively maintains two large databases: Hosts (nodes/services) and Certificates (certificates). Thanks to this, Censys can find, for example, all domains where a specific certificate is used or monitor the emergence of new self-signed certificates on IoT devices.
Data Structure and Accuracy
Since Censys originates from an academic environment, it collects maximally structured data. A record about a node is presented as a JSON object, which includes a services section - a list of all open services on the host with detailed descriptions of each. For HTTPS, this includes the full certificate and its parameters (algorithms, cipher suites, supported TLS versions); for SSH, it includes supported algorithms and keys; for databases, it includes the DBMS version and some configuration parameters, etc. Censys actively correlates data: for example, it identifies virtual hosts - if one IP serves multiple domains (through the SAN certificate fields or HTTP Host), those domains are also counted as separate records. This results in a very large total number of records in Censys. For instance, considering virtual hosts, Censys has over 1.4 billion records for HTTPS (port 443). However, for practical tasks, virtual duplicates are usually filtered out: when counting unique IPv4 addresses, Censys detects about 50 million hosts with web ports, ~21 million with SSH, ~24 million with Telnet/CWMP, etc. - figures close to Shodan. This indicates a high completeness of Censys's coverage: it's at least on par with Shodan in terms of the number of active IPv4 nodes and in terms of data (e.g, the presence of TLS), it surpasses it.
Search Language and Interface
In 2022, Censys introduced a new query language - Censys Search Language, which unified the search for hosts and certificates. Previously, searches were conducted through separate interfaces (and APIs) for Hosts and Certificates; now, conditions for both can be combined in a single query. Queries in Censys can be made using simple string searches (similar to Shodan) or as logical expressions based on fields. For example, a simple query like "Apache httpd 2.4.X country:US" will find all banners for Apache 2.4.xx in the United States (string search for banners + country filter). However, the true power of Censys lies in structured searches through JSON fields. For instance, one could write: services.service_name: "HTTP" AND services.http.response.status_code: 200 AND location.country_code: "US" to find only hosts in the US that have HTTP open and where the web server responds with a status code of 200 (OK).

*a screenshot demonstrates an example of using an advanced query in Censys:
host.services.protocol:"HTTP" AND host.services.endpoints.http.status_code="200" AND location.country_code:"US".
Moreover, regular expressions and ranges are supported. For example, one can find all certificates issued to domains of the form *.gov.br (Brazilian government sites) that are expiring in less than 30 days - such queries have been described in researcher's blogs. The Censys interface (web portal) is quite minimalist: searching is done through a single line and results are displayed in tables or cards with the option to switch to detailed JSON. Many engineers find it more convenient to use the API directly or download complete datasets (Censys periodically publishes data dumps for research purposes).
Availability and Pricing
Censys offers a free Community account, which is sufficient for basic queries. The limit in the free mode is 250 search queries per day (previously it was per month, but the model has changed) and access to most fields (except for very specific ones). The API is also available for free for these 250 requests/day with authentication. This volume is generally enough for one-time research and scripts. Commercial plans for Censys are aimed at large companies: exact prices are not disclosed (typically several thousand dollars per month and higher).
Examples of Use
Censys is particularly favored by vulnerability researchers and academics. It's often used to measure the global prevalence of specific issues. For example, immediately after discovering a critical vulnerability (like Heartbleed or Log4Shell), experts use Censys to execute complex queries and count how many hosts on the internet remain vulnerable - these statistics are frequently cited in the media. Thanks to its certificate index, Censys allows for actions that are impossible in Shodan: for instance, finding all websites where the certificate contains the name of organization X (in the Subject or Issuer field). This aids in OSINT - identifying related domains of a company through certificates. Censys is also actively used for inventorying external assets: since it scans all ports, one can discover not only the usual 80/443 but also, say, a forgotten open RDP (3389) or an admin port of a custom application on port 8443, which Shodan might not have checked. Large companies regularly conduct audits of their networks using Censys. Overall, Censys is considered the "gold standard" in terms of data completeness. It answers the question "what exactly is running on this host?" in the most detailed manner. However, its use requires more experience due to the complexity of queries and the vast amount of information. Security engineers often combine Censys with Shodan: they perform a quick initial search on Shodan and then clarify details (service configurations, certificates, all ports) through Censys. This approach ensures both speed and depth.
General Overview
FOFA (Eye of the Fox, Fingerprint Of All) is another representative of Chinese cyber scanners developed by Baimaohui, the organizer of the White Hat conference in China. Launched around 2017, FOFA gained recognition for its extensive coverage and ability to search through the content of banners and web pages. Many specialists in Russia discovered FOFA as an alternative to Shodan after several high-profile leaks were found specifically through FOFA, such as data leaks from unsecured Elasticsearch and Kibana instances that Shodan didn't index properly at the time. Initially focused on the Chinese internet segment, FOFA now features an English interface, similar to ZoomEye.
Index and Coverage
The name Fingerprint Of All reflects the service's goal of collecting "fingerprints" from everything available. FOFA scans the global IPv4 (and likely selectively IPv6, although exact details are not disclosed) similarly to Shodan. The number of ports is not explicitly stated, but it's known that FOFA indexes over 1200 ports, including rare ones. In tests conducted by the Netlas team, FOFA successfully covered the entire list of ports scanned by Shodan and even had its own additional list. Thus, in terms of port coverage, FOFA is comparable to Censys/ZoomEye (possibly not scanning all 65k, but more than sufficient for practical use). The update frequency for FOFA varies: more popular ports are scanned frequently (up to daily), while exotic ones may remain unupdated for several weeks. Developers have mentioned that priorities are set based on the prevalence of services. This means that FOFA, like Shodan, may have slightly outdated data on rare protocols but provides a fresh picture for the main ones. Overall, FOFA's coverage of unique nodes is comparable to Shodan (tens of millions of active hosts), although the service boasts "over 4 billion records" in its database (FOFA Reviews - 2025), likely counting all protocols, historical data, etc. FOFA also has a vast database of fingerprints - over 350,000 templates for identifying software and devices through banners (FOFA Reviews - 2025), successfully identifying many products, including those from Chinese manufacturers that are not always recognized in Shodan.
Search Language
FOFA offers a rich query syntax, quite similar to Shodan but with its own specifics. Notably, filters can be written in both English and Chinese, catering to different audiences. For example, the query ip="8.8.8.8" is equivalent to ip.addr="8.8.8.8" and will find the specific IP.

*a screenshot demonstrates the search results for the IP address 8.8.8.8 in the FOFA interface. The results display information about the services, banners, the owning organization (in this case - Google), as well as the protocols used (443/HTTPS).

*a screenshot demonstrates the query body="password" in FOFA - one of the classic dork queries that allows users to find web pages containing fields for password input. This can be useful for identifying open login panels, vulnerable pages, or configuration interfaces.
Interface
FOFA has two web addresses: the Chinese fofa.so and the English fofa.info. After logging in, users can switch to the desired language. The interface is quite simple: a search bar and a dropdown list of filters. Results are displayed in a list format, where each line is either an IP: Port or domain: Port, along with a short snippet of the banner. An interesting detail is that FOFA by default shows not the entire banner but only the part where the search condition matches, highlighting the found string. This is convenient for text searches, but sometimes it may seem like there is little data - users need to click on the entry to see all fields in full. The host card presents all collected information: IP, ports, services, banners, domains, geolocation, etc. Paid users can export results in CSV/Excel format. Like ZoomEye, FOFA retains historical data: users can see when a host was first and last observed and how its banners changed over time.FOFA has a mobile application and even a desktop client (primarily aimed at Chinese users). The client includes a unique PoC accelerator - a store of exploits that allows users to immediately check found hosts for vulnerabilities (for example, by clicking and launching a ready-made exploit against a host). This is closely integrated with the Chinese ecosystem and is little used outside of China, but it demonstrates how advanced local tools aim to be.
Access and Limits
A free FOFA account allows users to perform searches without request limits, but results are restricted to the first 100 entries. This means users will only see a small portion of the results before receiving a message stating "VIP required". For full functionality, a paid subscription is necessary. The pricing tiers include Personal VIP, Enterprise VIP and others. The basic personal account costs around $100 per year and allows viewing up to 10,000 results per query and using the API (with a limit, for example, of 1,000 API requests per day). Higher tiers (Corporate, Enterprise) increase limits - up to 100,000 results and unlimited API access for Enterprise. A significant advantage of FOFA over ZoomEye is the absence of artificial restrictions on scrolling through results: if you have VIP access, you can see all millions of results if they exist. In contrast, ZoomEye doesn't allow exporting more than a certain ceiling even with a paid account (for security reasons, to prevent downloading the entire database). Additionally, FOFA doesn't restrict queries on Chinese addresses: it is known that ZoomEye may hide some results related to critical infrastructure in China for political reasons, while FOFA is more open.
Unique Features
FOFA has several "features" that outpace its Western competitors. For instance, FOFA was one of the first to implement search by website icon (favicon hash). Users can upload a favicon.ico file in the interface and the service will find all hosts with the same icon hash - extremely useful for identifying similar web applications (e.g, admin panels of a specific product). Shodan later added such a function (http.favicon.hash), but FOFA was the pioneer. Another feature is the alerts system: users can save any search query and enable monitoring, allowing FOFA to send notifications when new results matching that query appear. This effectively serves as a tool for tracking one's resources or the emergence of new vulnerable devices based on specified criteria. FOFA is also developing a knowledge library (FOFA Library) - a section where articles and use cases are published (mostly in Chinese). For example, cases of mass scanning of government websites or searching for specific vulnerable devices on the internet have been discussed there, helping new users learn. FOFA also offers integrations: there is a plugin for BurpSuite (allowing users to search for exposed subdomains from the Burp interface), modules for Nmap, plugins for radiographic analysis (Radare) and more. The community around FOFA actively shares scripts and fingerprints.
Examples of Use
FOFA is often preferred for searching for information that Shodan does not find. Primarily, this includes textual content on pages. For example, if you need to find all web interfaces of devices where a specific phrase appears on the page - Shodan will not help with banners, but FOFA will handle the query body="phrase". This has been used to find leaks of confidential data on forgotten pages, identifying interfaces with error messages containing keywords (e.g, "SQL error"). FOFA is also more useful for searching devices in the Asian internet segment: it better recognizes equipment from local brands, has a more complete database of Chinese ASNs and is actively used by local researchers. Therefore, if something appears in Chinese networks, it almost immediately gets indexed by FOFA. For OSINT on Chinese companies, FOFA is a must-have tool, while Shodan may miss parts of the infrastructure. Of course, FOFA cannot completely replace Shodan - its index also has gaps and the data refresh rate is somewhat inferior (on less popular nodes). Therefore, professionals often use them in tandem.
Conclusion
Conclusion
Censys and FOFA represent two completely different approaches to the problem of internet inventory. Censys maintains academic rigor and structure, providing highly accurate data with a high degree of detail, making it ideal for analytics, inventory,and vulnerability research. FOFA, on the other hand, emphasizes the breadth of coverage, flexibility of query language and content search capabilities - an indispensable function for OSINT and leak detection. Both platforms complement each other excellently. Using them in tandem allows users to address both monitoring tasks and OSINT, bug bounty and the search for specific assets on the internet. In the next part of the review, we will explore newer but actively developing solutions: Netlas and Criminal IP, which offer interesting approaches to searching, visualizing and analyzing digital footprints.